In this tutorial, we will look at how to install Tailscale on TrueNAS Scale.
Tailscale is a zero-configuration VPN, which means that without any port forwarding, you’ll be able to access all the devices on your local network. Running Tailscale on TrueNAS Scale is a great option as you can configure the application, connect it to your Tailscale account, and then access your local network.
Tailscale is a great option for anyone, though there are some users who have a CGNAT where using Tailscale is necessary for VPN connectivity.
How to Install Tailscale on TrueNAS Scale
The steps below will explain how to install Tailscale on TrueNAS Scale using Truecharts.
Tailscale Settings
1. Before we proceed, we need to configure the pre-authentication key. This can be created on the Tailscale website. If you don’t already have an account, create one, then log in and select Settings, then Keys.
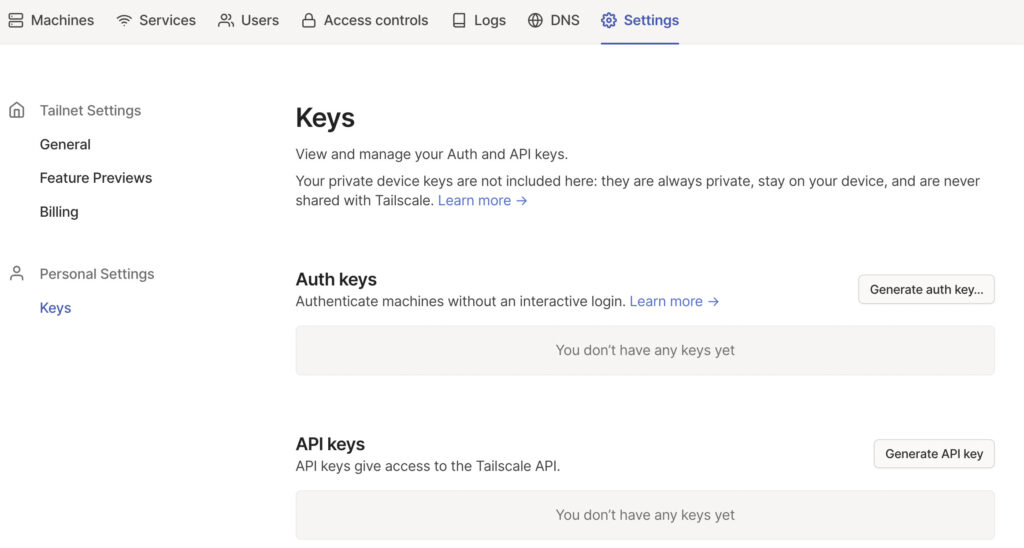
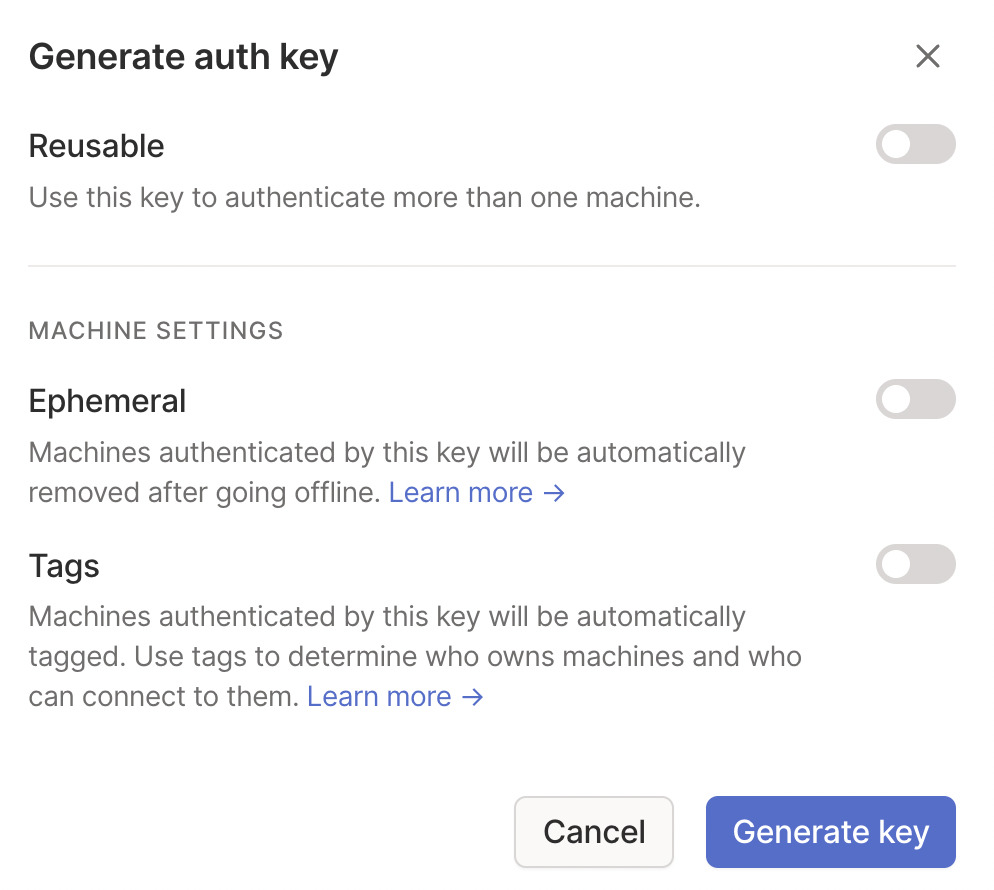
2. Select generate auth key so that we can create the key for Docker. Select Generate Key (the settings can stay as default).
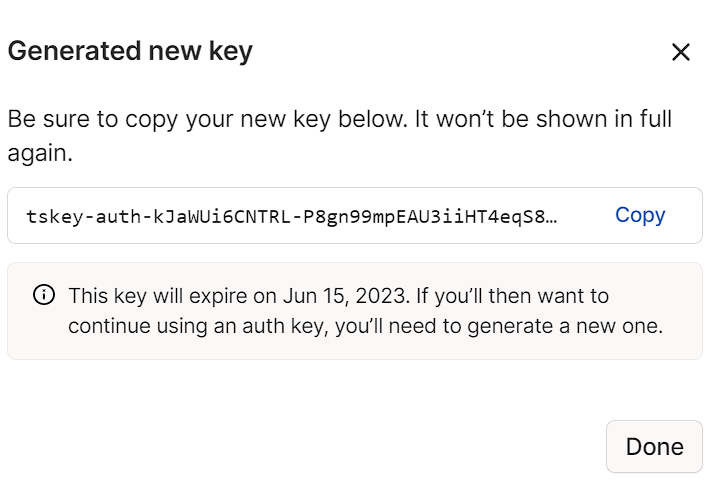
3. After the key has been generated, copy it, then proceed to the TrueNAS configuration.
Setting up Truecharts on TrueNAS Scale
In order to configure Tailscale, the easiest way is to use Truecharts. To install that, you must follow the instructions below.
Please keep in mind that this is not a default package. Check out the Truecharts website to determine if you’d like to proceed with this approach, but this is the only functional way I know of installing Tailscale on TrueNAS at this point (installing it manually through the CLI breaks after a reboot).
To add the Truecharts catalog, select Add Catalog, then paste the path below in the Repository section. Give the catalog a name, then Save.
NOTE: As mentioned above, this is not officially supported.
https://github.com/truecharts/catalog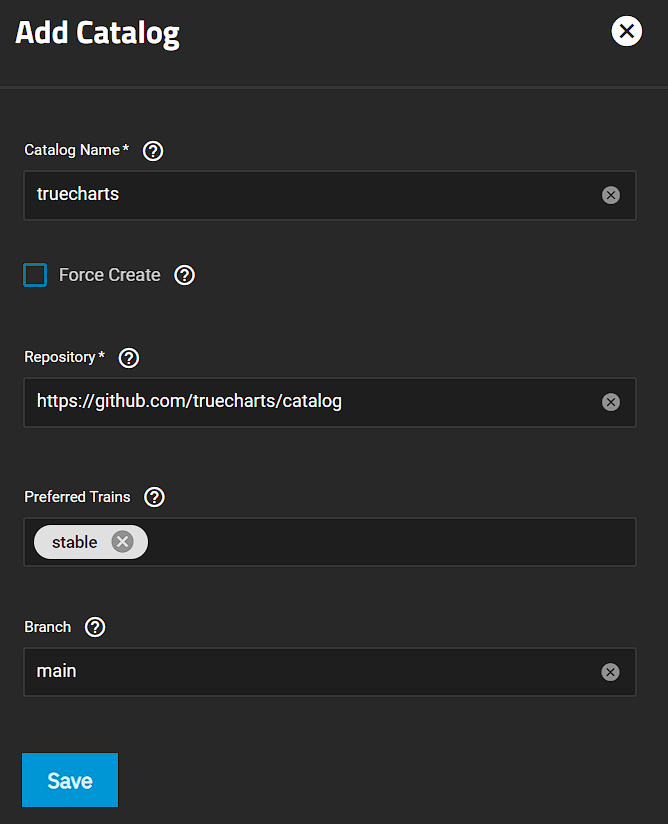
After a few minutes, the Truecharts applications will display and you’ll notice that there are a lot more Apps than there used to be. One of those Apps will now be Tailscale.
Setting up Tailscale on TrueNAS Scale
Now that Truecharts is installed, we can install the Tailscale package.
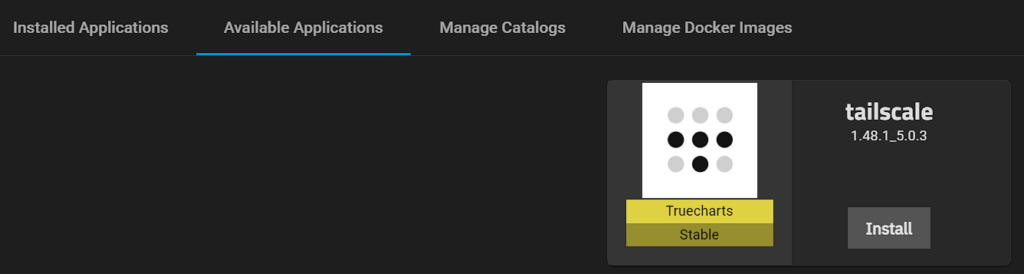
1. Access the Available Applications, search for Tailscale, and then select Install.

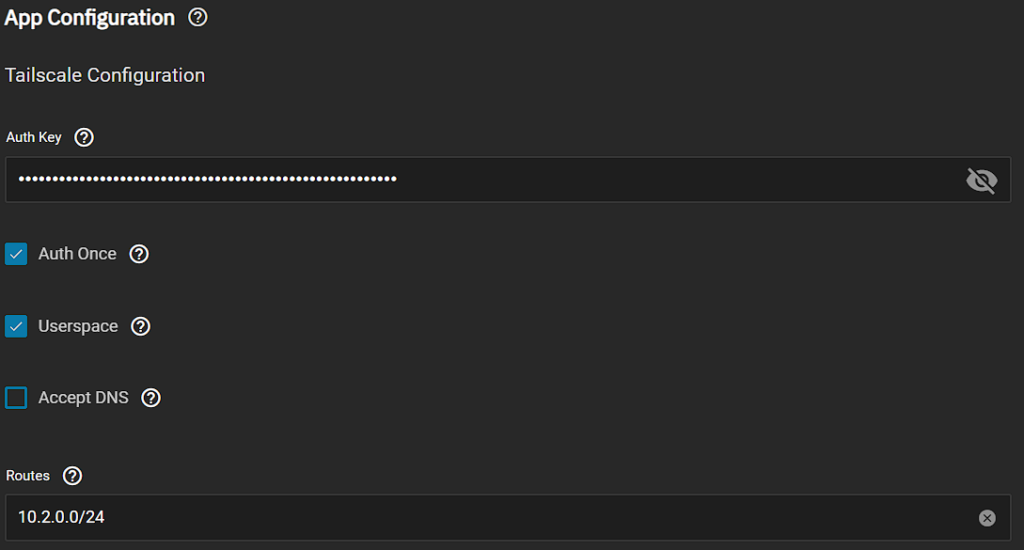
2. In the App Configuration section, paste in the Authentication Key we got above. If you plan on using TrueNAS as an exit node, you must keep the Userspace option enabled as well.
Keep in mind that there are other limitations if you enable the Userspace, so confirm in the Truecharts documentation if you do or do not want to enable it.
In the Routes section, add the routes (local IPs) that you’d like to access through this Tailscale tunnel.
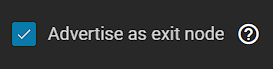
3. If you’d like this to be used as an exit node (for a full tunnel VPN), you must enable the option.
4. The rest of the settings can stay as default. After selecting Save, the Tailscale container will be created.
Please keep in mind that Truecharts is an open-source project that you might want to consider supporting.
Exit Node/Subnet Routes
If you set up Tailscale as an Exit Node (or simply access the local subnet), there are additional settings that must be configured. If you configure an Exit Node, it can be used as a full-tunnel VPN.
The image below shows what a full-tunnel vs split-tunnel VPN is, but the important point is that all traffic will be routed through Tailscale if you use an exit node.
Therefore, if you’re on public Wi-Fi, it’s probably a good idea to use this feature as you’ll be tunneling all traffic through the Tailscale tunnel (thus, securing the connection).
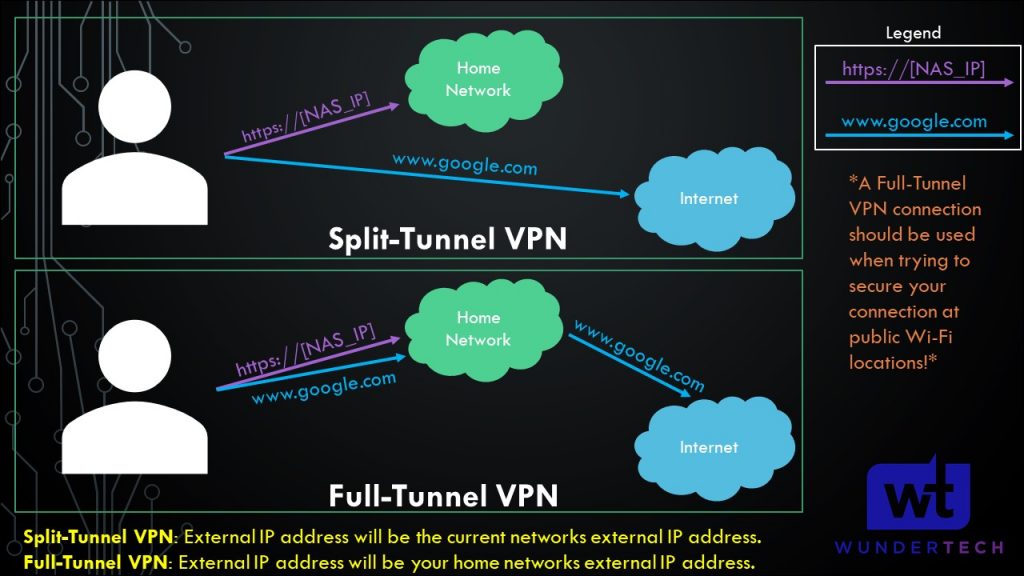
A few things must be configured to set up subnet access (split tunnel) or an exit node (full tunnel) in Tailscale:
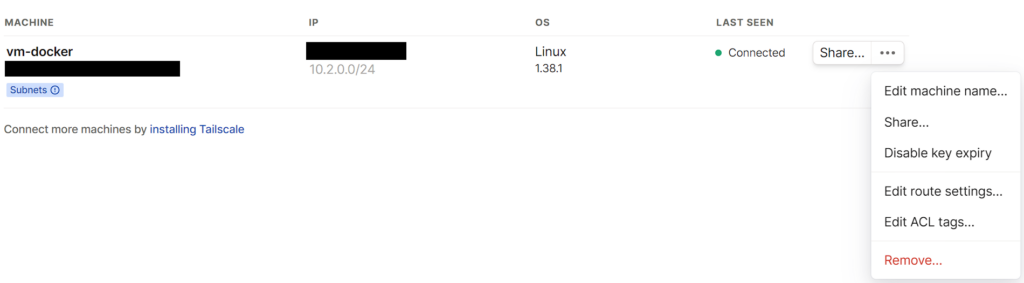
1. On the Tailscale website, select Machines, then the three ellipses next to your Docker system, then Edit Route Settings.
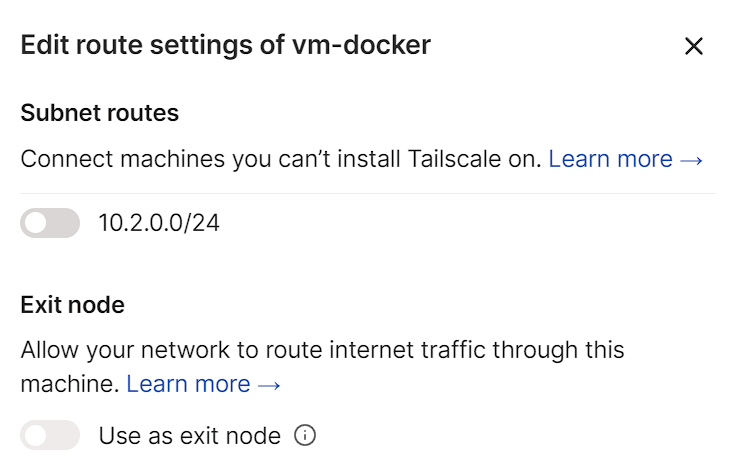
3. If you want to use a full-tunnel VPN, select the subnet route and use as exit node. This will configure a full-tunnel VPN.
If you only want to use a split-tunnel VPN (meaning only being able to access the 10.2.0.0/24 subnet in the screenshot below), select that option, but do not select the “use as exit node” option.
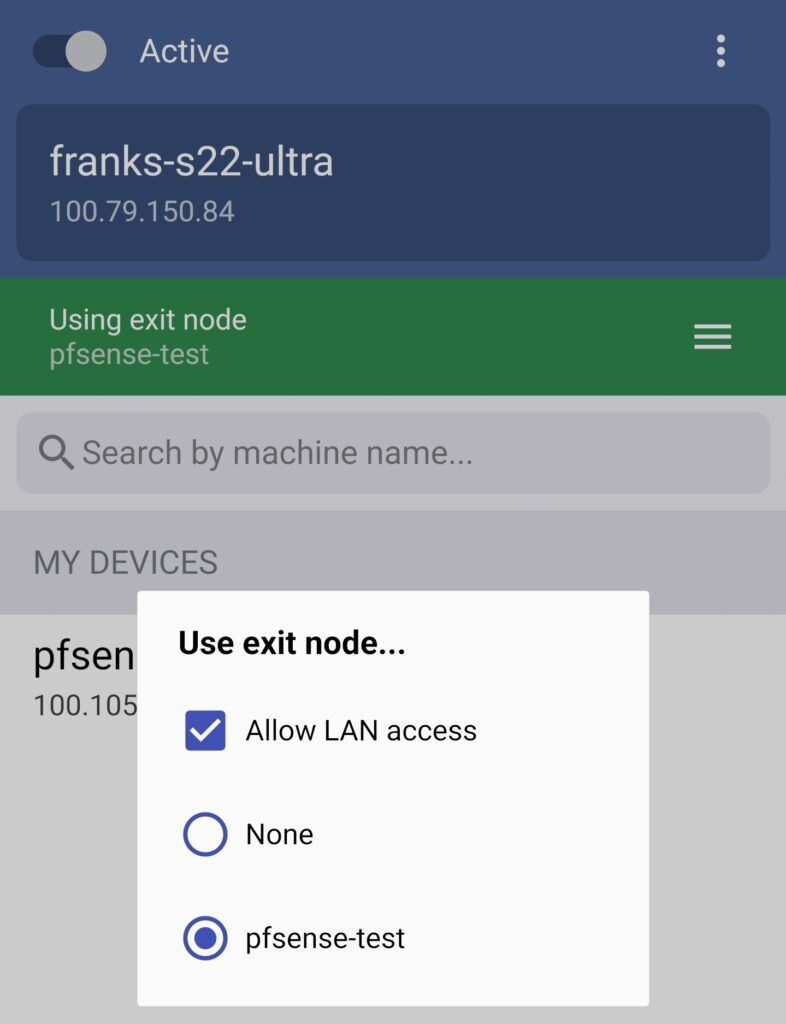
4. If you do want to use an exit node, select Use Exit Node (on whatever application you’re using) and change the exit node to be the TrueNAS machine.
If you do not want to use the exit node, select None, but ensure that Allow LAN Access is enabled so that you’re able to connect to your local devices.
NOTE: The screenshot below uses pfSense, but it’ll be the same for your TrueNAS configuration.
5. Tailscale is now configured! You can now add other devices or simply connect to Tailscale from an external network to access all of your local devices.
Conclusion: How to Set Up Tailscale on TrueNAS Scale
This tutorial looked at how to set up Tailscale on TrueNAS Scale. Tailscale couldn’t possibly be easier to set up and it’s (in my opinion) the easiest and fastest way of setting up a VPN server on almost any device.
It is important to note that this isn’t a traditional VPN the way that OpenVPN or WireGuard is (which can be run on routers like pfSense or OPNsense), but it’s the fastest way to access your local network and doesn’t require any port forwarding.
Thanks for checking out the tutorial on how to set up Tailscale on TrueNAS Scale. If you have any questions on how to set up Tailscale on TrueNAS Scale, please leave them in the comments!




