This article will look at split tunnel vs full tunnel VPNs to help you determine which option is best for you. When you configure a VPN, you’ll have two options for VPN types that you can configure and use: split tunnel or full tunnel. The way that these two VPN types operate is drastically different, and it’s important to understand exactly how they function before configuring your VPN.
Split Tunnel vs Full Tunnel VPNs
We will look at the key differences between split-tunnel and full-tunnel VPNs below.
Split Tunnel VPNs
A split tunnel VPN is generally configured by setting specific subnets to send through the VPN tunnel. All other traffic that is not included is sent through the network the device is connected to, without going through the VPN tunnel.
For example, if you configure a split tunnel VPN to only route traffic for the 192.168.10.0/24 subnet, the VPN tunnel will only be used if you’re attempting to access a device on the 192.168.10.0/24 subnet. All other traffic is routed through the network you’re connected to.
Split tunnel VPNs can be viewed as a good or bad thing depending on the requirements you have, but here are some general pros and cons.
| PROS | CONS |
| Only the traffic destined for the network where the VPN is hosted will be sent through the VPN tunnel. | You cannot secure a connection that you don’t trust (hotel, library, etc) by connecting to a split tunnel VPN. |
| If the network where the VPN tunnel is hosted is metered (pay based on data used), full tunnel VPN clients will add to the data usage, but won’t with a split tunnel VPN. | IP addresses may periodically change, so there is generally maintenance to ensure that split-tunnel VPNs continue operating as expected. |
| The performance will be faster for general web browsing. |
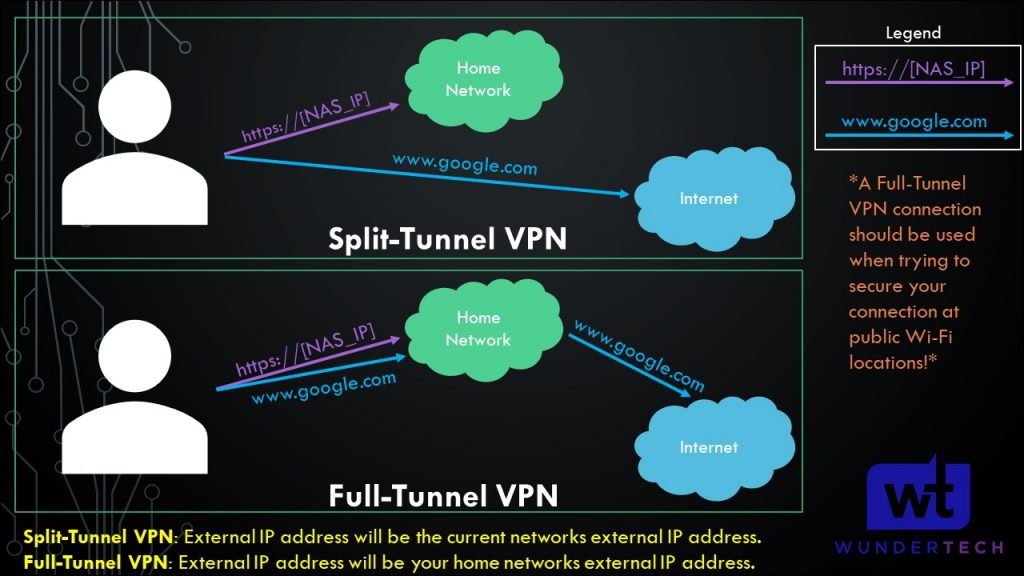
Your external IP address on a split tunnel VPN will be the IP address of the network that you’re currently on.
Split Tunnel VPN Example
The image below shows a WireGuard split tunnel VPN (configured on pfSense). The AllowedIPs section is listed as 10.200.0.0/24 and 10.2.0.0/24.
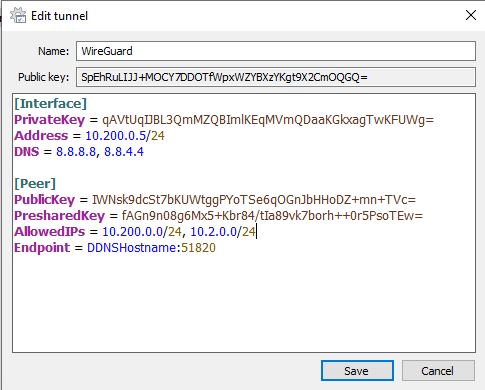
The only traffic that will be routed over this VPN tunnel is the 10.200.0.0/24 and 10.2.0.0/24 subnets. All other traffic will route through the internet on the local network.
Full Tunnel VPNs
A full-tunnel VPN is the complete opposite of a split-tunnel VPN. While a split tunnel VPN selectively determines which traffic should and should not be routed over the VPN tunnel, a full tunnel VPN will route all traffic over the VPN.
Here are a few pros and cons of using a full-tunnel VPN.
| PROS | CONS |
| You can secure a connection that you don’t trust (hotel, library, etc) by connecting a full tunnel VPN. | If the network where the VPN tunnel is hosted is metered (pay based on data used), VPN clients will add to the data usage. |
| Less maintenance overall, as there’s no requirement to maintain a list of IP addresses that should use the VPN. | If you don’t have to secure a connection (meaning you’re on a trusted network), you’re routing all traffic through the VPN tunnel which might not be necessary. |
| The performance will be slower for general web browsing. |
Your external IP address when connected to a full tunnel VPN will be the IP address of the location where the VPN server is hosted.
Full Tunnel VPN Example
The image below shows a WireGuard full tunnel VPN (configured on pfSense). The AllowedIPs section is listed as 0.0.0.0/0, which will route all traffic over the VPN tunnel.
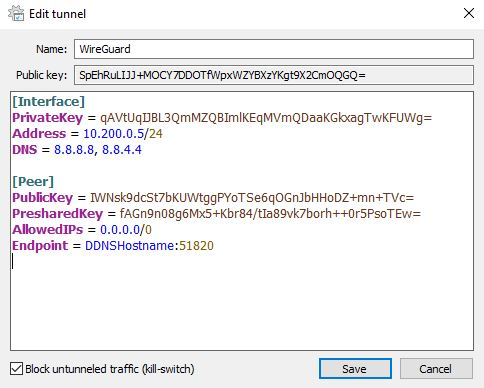
Split Tunneling vs Full Tunneling
When comparing split tunneling vs full tunneling, you really have to determine exactly what you’re trying to accomplish with this VPN tunnel.
For example, in an enterprise environment where there might be VoIP calls, a split-tunnel VPN makes more sense, as you might have performance issues with a full-tunnel VPN (as VoIP can be sensitive to network performance).
However, a full tunnel VPN provides security enhancements that a split tunnel VPN won’t, so while performance is one consideration, so is security.
Overall, the requirements you have should determine if a split tunnel or full tunnel VPN should be used, but most people will be happy with a split tunnel VPN if accessing devices using the VPN is the only goal.
Split/Full Tunnel VPN Example
This shows an example of the network flow differences between a split tunnel vs full tunnel VPN. Notice how all traffic is routed over the VPN when connected to a full tunnel VPN.
NOTE: This is not the exact network flow, but a simplified version.
Conclusion & Final Thoughts: Which VPN Type to Use?
The article above looked at some of the differences between split-tunnel vs full-tunnel VPNs. In general, most people should set up both if possible, which allows you to connect to the full-tunnel VPN when you need to secure your connection, or the split tunnel when performance is important. This provides the best of both worlds, but if security is important on external networks, go with a full-tunnel VPN.