In this article, we will look at how to set up WireGuard on UniFi Devices.
WireGuard is a VPN tool that’s faster, simpler, and leaner than something like OpenVPN. Where OpenVPN has the benefit of longevity, WireGuard is the newer, faster VPN protocol that many people are looking to try and it’s officially supported on UniFi devices.
While we are diving into how to set up WireGuard on UniFi devices in this tutorial, please be aware that this is a newer implementation and while everything has worked for me, you might run into some problems. If you want to ensure that you can always access your local network, please consider setting this up with L2TP as well. This way, you are ensuring that you’ll always be able to connect.
Disclosure: Some links below are UniFi affiliate links which means that I earn a percentage of each sale at no cost to you. Thank you for your support.
How to Set Up WireGuard on UniFi Devices
We will look at how to set up WireGuard on UniFi Devices below with the newly supported WireGuard VPN process!
1. Open the UniFi Controller and select Settings.
2. In the settings menu, select Teleport & VPN.
3. In the VPN Server section, select Create New.
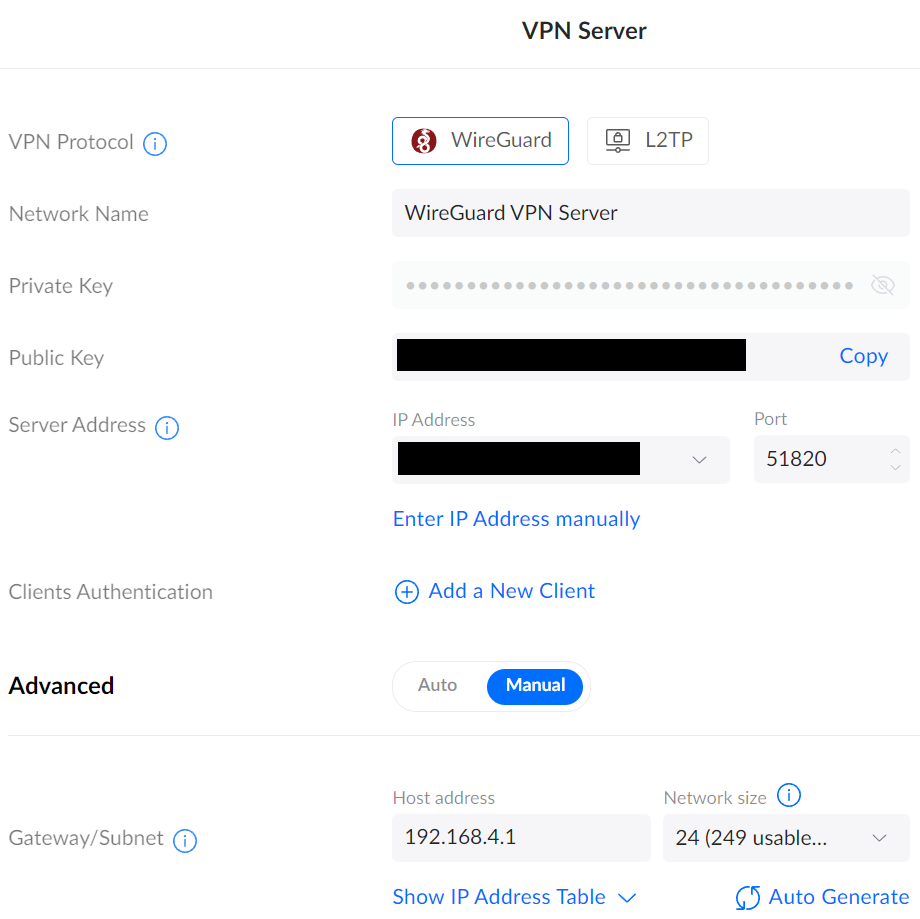
4. In this section, there are a few things you can change:
- Ensure that WireGuard is selected.
- Set the Network Name you’d like to use.
- Set the Port as 51820.
- If you’d like to change the subnet address, you can in the Gateway/Subnet section.
When the changes have been made, select Apply to enable the VPN server.
At this point, the WireGuard VPN server is fully configured. However, we must create a VPN client for each device that will be connecting.
WireGuard VPN Client Setup for UniFi Devices
Follow the instructions below for each client that you’d like to be able to connect to your WireGuard VPN Server.
1. Access the WireGuard VPN Server settings by selecting it, then select Add a New Client in the Clients Authentication section.

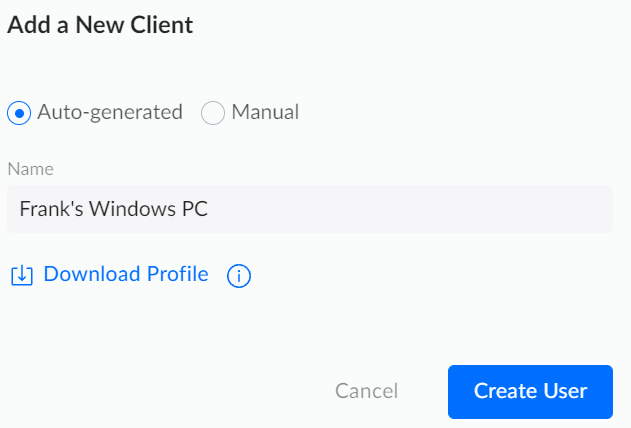
2. In the Add a New Client section, enter a Name and leave it as Auto-generated, then select Download Profile, and finally, Create User.
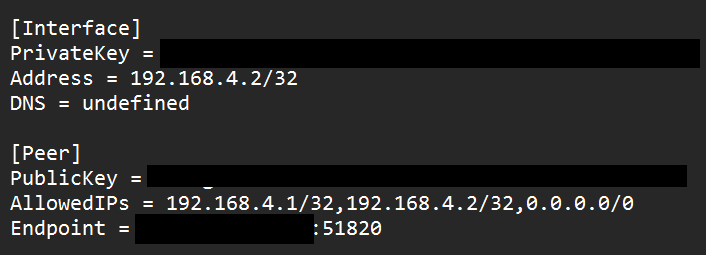
3. If you open the VPN Configuration file in a text editor, the contents will look similar to the information below. There are a few things that you should modify in this configuration file before using it:
- The DNS Server can be modified (by removing undefined and replacing it with an IP address) to whatever DNS server you’d like to use. Common public DNS servers are Google’s (8.8.8.8 or 8.8.4.4) or Cloudflare’s (1.1.1.1).
- If you have a Dynamic IP Address, you should replace the IP address in the Endpoint section with a DDNS hostname. A DDNS hostname will automatically point you to your external IP address, even if it changes.
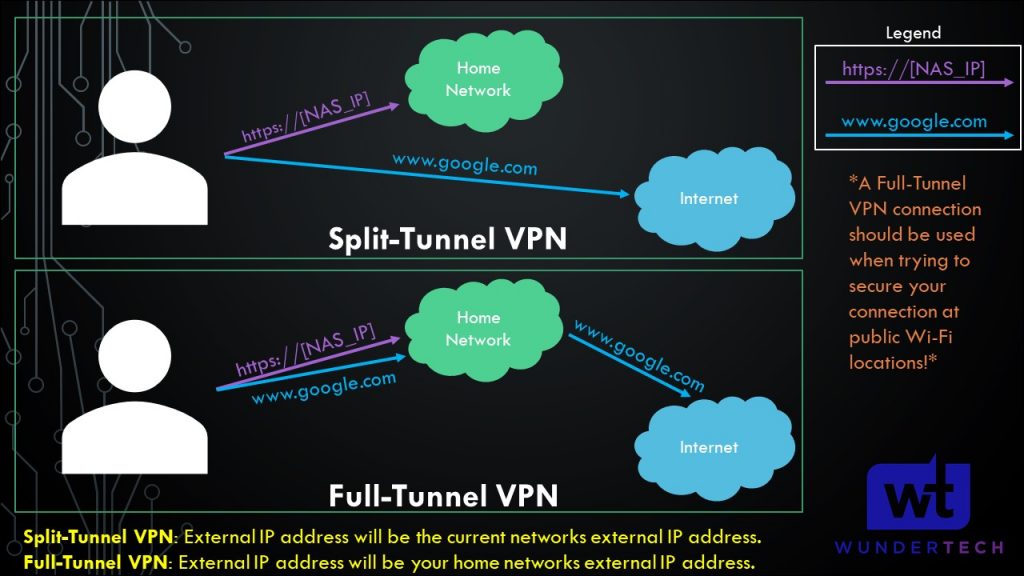
The final field that can be modified is AllowedIPs. This section will determine how the traffic is routed over the VPN tunnel. You can set up either a full-tunnel VPN or a split-tunnel VPN by modifying this field.
- Split-Tunnel VPN: Traffic is only sent through your network if it is attempting to access an internal resource. Your IP address when navigating to a site outside of your network will be the IP address of the network that you are currently on.
- Full-Tunnel VPN: All traffic is sent through your VPN tunnel. Your IP address for internal and external requests will be your home network. I created a very basic image below that explains this.
It’s important to understand that both VPN types will allow you to access your local network. This only shows how traffic is routed differently to external networks.
NOTE: This is not the exact network flow. I am simplifying the process as much as I can.
Split-Tunnel VPN Settings for WireGuard
In the AllowedIPs section, enter the IP addresses that you’d like sent through this VPN tunnel. At a minimum, this should be your VPN subnet (in our case, 192.168.4.0/24) and LAN subnet (so that you can connect to your local devices). Separate all subnets that you’d like to access by a comma.
With this configuration, your external IP address when navigating to websites will be the network that you’re currently on.
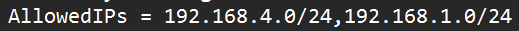
Full-Tunnel Client Configuration for WireGuard
If you’d like to route ALL traffic through the VPN tunnel, set the AllowedIPs parameter to 0.0.0.0/0. This will route all traffic through the VPN tunnel.
With this configuration, your external IP address when navigating to websites will be the UniFi network’s external IP address.
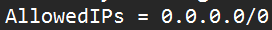
After configuring these changes and saving the file, you should be able to open it on a WireGuard device and connect! Everything else should be configured properly, so as long as the settings above on the client side are adjusted, you’ll be able to access your local network through WireGuard!
Conclusion & Final Thoughts on Configuring WireGuard
This tutorial looked at how to set up WireGuard on UniFi devices. This is a new implementation (though there technically were ways to do it in the past), and is an extremely easy setup compared to other WireGuard setups I’ve done (like pfSense). If you are using a UniFi router and would like to set up a VPN on it, I’d really suggest looking into WireGuard.
Thanks for checking out the tutorial on how to set up WireGuard on UniFi devices. If you have any questions, please leave them in the comments!




