In this tutorial, we will look at how to set up OpenVPN on a Synology NAS. After my recent Ultimate Synology NAS Setup & Configuration Guide tutorial, I received a ton of great feedback from users who were interested in safely and securely accessing their NAS from outside of their network.
I’ve been using OpenVPN on a Synology NAS using the VPN Server package for the past year and have had no issues at all. I can safely access my NAS anywhere in the world and more importantly, I control access. This OpenVPN on a Synology NAS setup tutorial is not for a privacy VPN like NordVPN, but instead for a personal VPN to access your services from outside of your local network.
OpenVPN on a Synology NAS Step-by-Step Guide
The six steps below will walk you through the process of how to set up OpenVPN on a Synology NAS following best practices.
Step 1: Install the OpenVPN Package on a Synology NAS
The first step when looking at how to set up OpenVPN on a Synology NAS is installing the VPN server package.
- Open the Package Center and Install the VPN Server application.
- Open the application and navigate to the OpenVPN section.
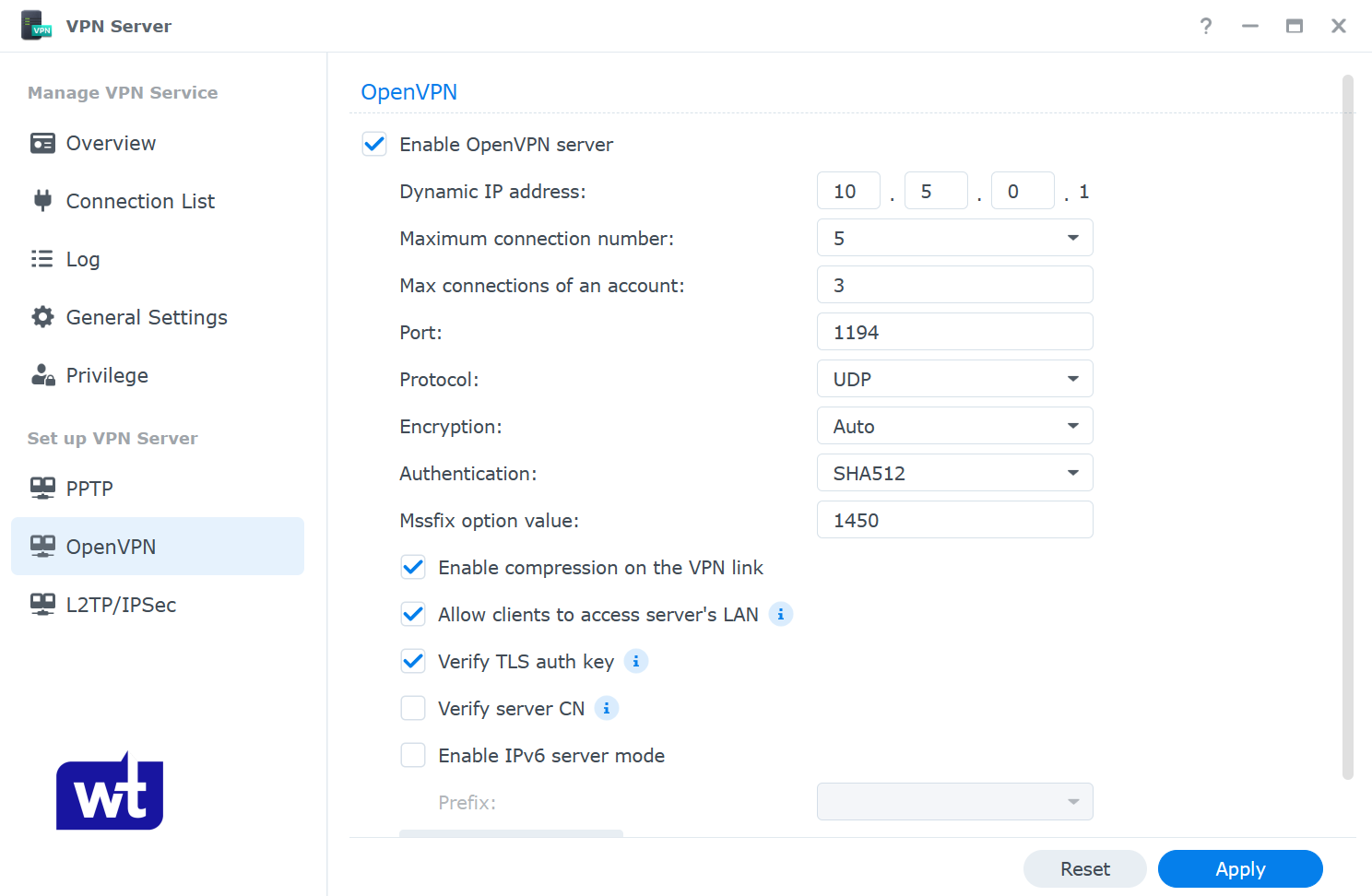
- Enable OpenVPN Server. Change the Dynamic IP address range and maximum connection properties if you’d like.
Since we are trying to access our Synology NAS outside of our network, we need to enable Allow clients to access server’s LAN, as well as Verify TLS auth key. The rest can stay as default. Click Apply.
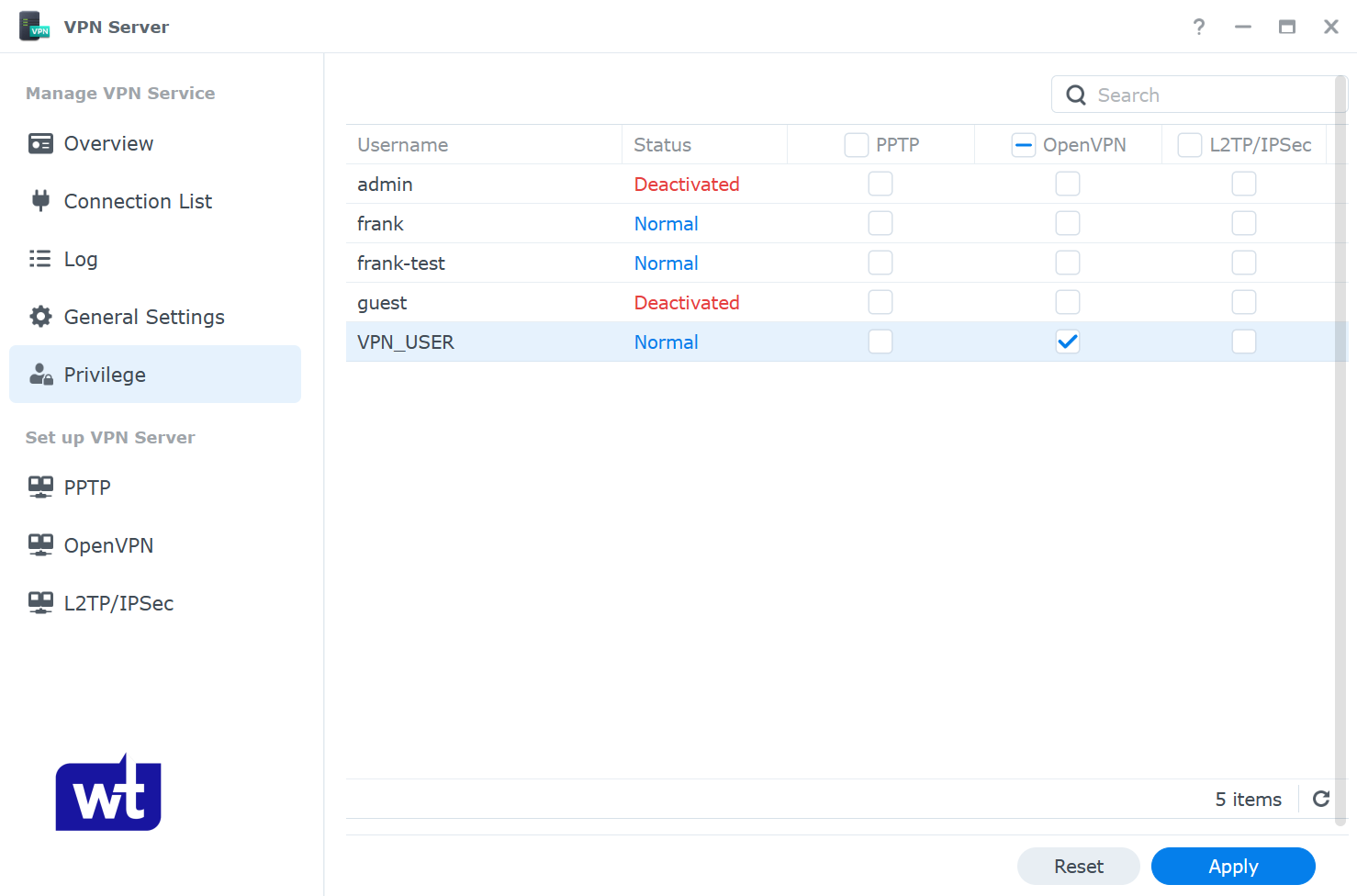
- Navigate to the privilege section and ensure that the user account that you’d like to connect to the VPN with has permission for OpenVPN.
NOTE: I normally configure an individual user that has permission to the VPN server ONLY. This ensures that I connect to the VPN server with this user, and then access the NAS and everything else using my regular NAS username. You do not have to do this, but this is how I normally manage it.
Step 2: Configure Synology’s Firewall for the OpenVPN Port
Now that the OpenVPN on a Synology NAS package is now configured, we need to ensure that our firewall allows access to UDP port 1194. If you aren’t sure how to configure Synology’s Firewall, you can follow this tutorial.
- If you are using Synology’s firewall, open the Control Panel, Security, then navigate to the Firewall and Edit Rules.

- Create an Allow rule for the VPN Server (OpenVPN) application, UDP port 1194.
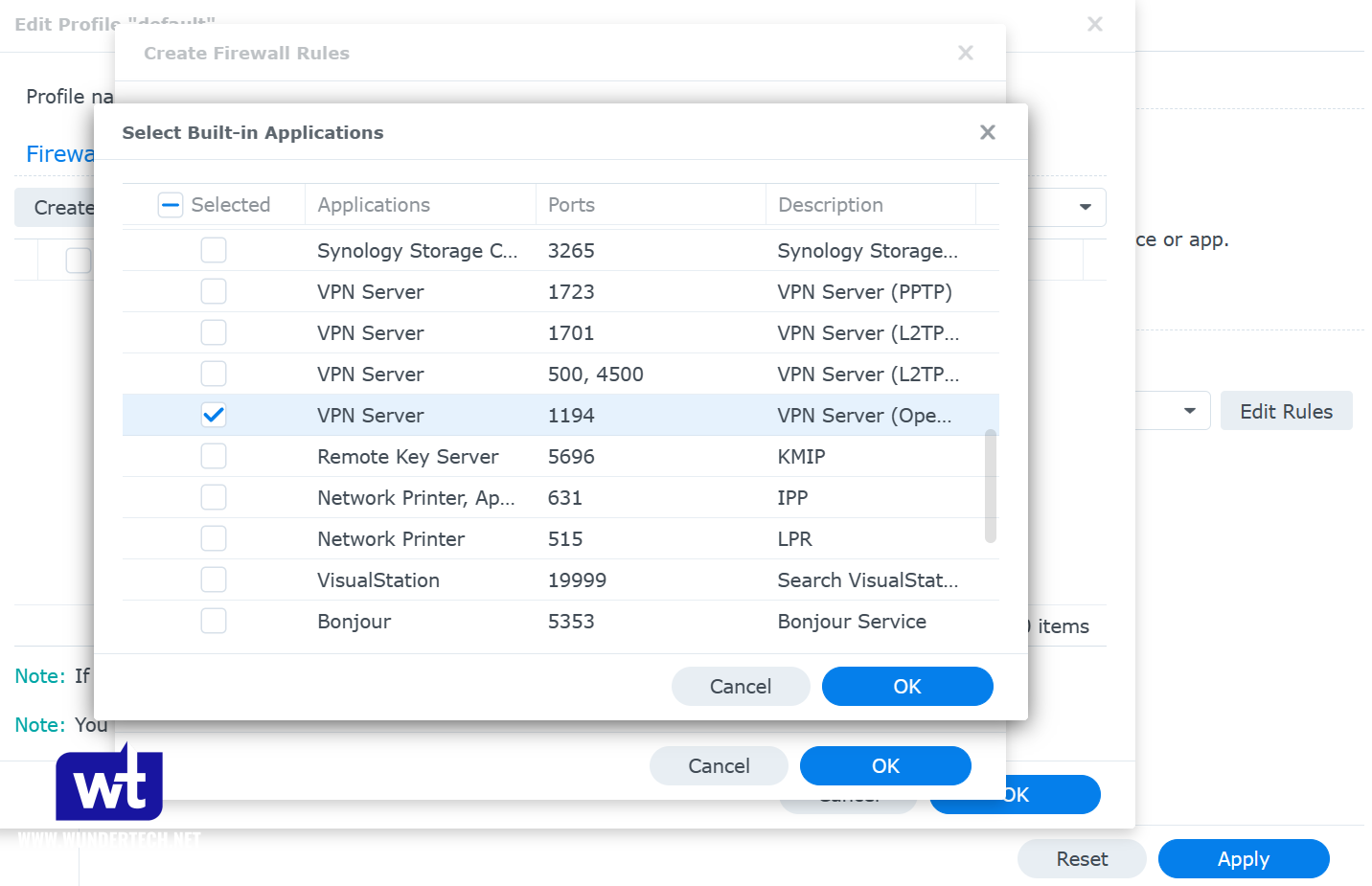
- When completed, the rule should be above the deny all rule.
Step 3: Port Forward the OpenVPN Port on your Router
We just configured our Synology firewall to allow connections on UDP port 1194 so that we can connect to OpenVPN on a Synology NAS.
We now need to port forward UDP port 1194 on our router to our Synology NAS. Synology has UPnP functionality, which gives your NAS the ability to open ports on your router automatically. If you have a UPnP compatible router, it’s very easy to set this up.
However, there is a lot of debate on the security of UPnP, so I will not be going over it in this tutorial. If you’d like to do it this way, you can read Synology’s help article here.
Now, port forwarding will be completely different on every brand’s router settings page. This is a great guide that shows how to port forward on a few different brands of routers, but the best thing to do is try and google the name of your router and port forwarding. Example: Netgear port forwarding
This process requires you to have a static IP address setup. If you don’t currently have a static IP address setup, read how to set up a static IP address here.
- Create a port forwarding rule for UDP port 1194 to your Synology NAS’s IP address. In the example below, 192.168.1.220 is the IP address of my Synology NAS.
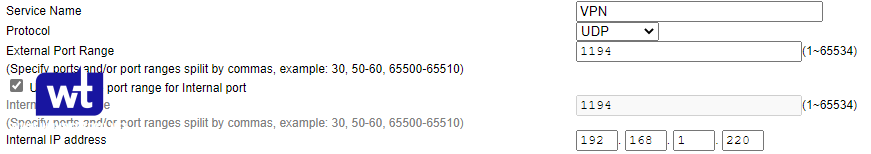
Assuming that you were able to open UDP port 1194 and configure the Synology firewall rule successfully, the port configuration is now complete!
Step 4: Modify the OpenVPN Configuration File
Now that we have configured OpenVPN on a Synology NAS, we need to modify our configuration file. Before we get into the steps, you need to ensure that you have DDNS configured.
Most people have dynamic external IP addresses, so creating a DDNS hostname is required because you need to ensure that you are always accessing your external IP address.
If you’d like to configure DDNS using a free synology.me hostname, you can follow Synology’s instructions here or this tutorial for DDNS (just don’t complete the port forwarding section in the DDNS tutorial).
If you are absolutely positive that you have a static external IP address that never changes, you do not have to set up DDNS. Simply use your external IP address as YOUR_SERVER_IP.
It’s also important to note that the DDNS provider is irrelevant, you just need to ensure that you have a DDNS hostname configured!
- Open the VPN Server application and select OpenVPN. Select Export configuration.
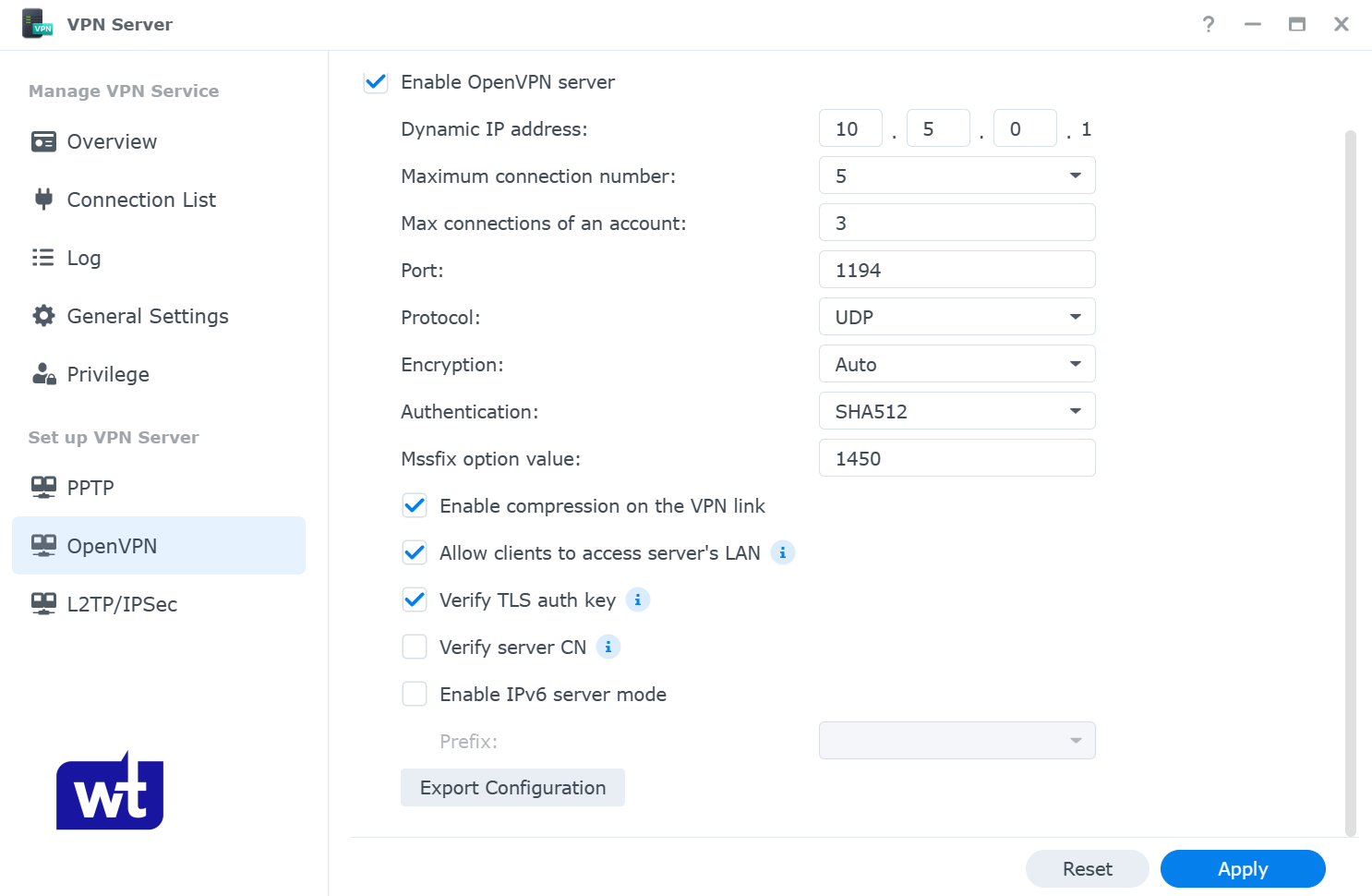
- Extract the contents of the folder. We will only be editing the Synology NAS OpenVPN .ovpn file, so open that file with a text editor.
- By default, you will receive a default Synology NAS OpenVPN configuration file with a unique certificate at the bottom. This document shouldn’t be shared with anyone other than users who you would like to authenticate with your VPN. We need to change the items below that are highlighted in red.
- YOUR_SERVER_IP: This should be the DDNS hostname that you configured.
- redirect-gateway def1: This is what determines if you are configuring a split-tunnel or full-tunnel VPN.
- I create two separate configuration files (one for split-tunnel and one for full-tunnel) and depending on the situation, use one or the other. To enable full-tunnel, remove the “#” sign (this is the symbol for a comment). Just removing the comment symbol will enable the full-tunnel VPN.
- NOTE: If you are using an iPhone and have iOS 7 or above, you will need to add redirect-gateway ipv6 under redirect-gateway def1.
- I create two separate configuration files (one for split-tunnel and one for full-tunnel) and depending on the situation, use one or the other. To enable full-tunnel, remove the “#” sign (this is the symbol for a comment). Just removing the comment symbol will enable the full-tunnel VPN.
- dhcp-option: If you have a local DNS server that you’d like to use, you can add the IP address of your DNS server there. If you don’t have a local DNS server, leave this line commented out.
- NOTE: If you don’t have a local DNS server configured, OpenVPN will default to using Google’s public DNS records (configured on the individual OpenVPN app).
- This means that you won’t be able to access any of your local network resources by hostname, only IP address. If you’d like to configure a local DNS server, you can check out my tutorial on Pi-hole here.
- NOTE: This is a very basic example of how DNS can be used.
- NOTE: If you don’t have a local DNS server configured, OpenVPN will default to using Google’s public DNS records (configured on the individual OpenVPN app).
- client-cert-not-required: This option is not added by default but should be added if you will be using the new OpenVPN clients (most people will be). If you don’t add this option, you will receive an error message when you connect. While you can proceed through the error message, this will stop the error from occurring.
This is a sample configuration file, but yours will look different.
dev tun tls-client remote YOUR_SERVER_IP 1194 # The "float" tells OpenVPN to accept authenticated packets from any address, # not only the address which was specified in the --remote option. # This is useful when you are connecting to a peer which holds a dynamic address # such as a dial-in user or DHCP client. # (Please refer to the manual of OpenVPN for more information.) #float # If redirect-gateway is enabled, the client will redirect it's # default network gateway through the VPN. # It means the VPN connection will firstly connect to the VPN Server # and then to the internet. # (Please refer to the manual of OpenVPN for more information.) #redirect-gateway def1 #redirect-gateway ipv6 #REQUIRED for iOS 7 and above. # dhcp-option DNS: To set primary domain name server address. # Repeat this option to set secondary DNS server addresses. #dhcp-option DNS DNS_IP_ADDRESS pull # If you want to connect by Server's IPv6 address, you should use # "proto udp6" in UDP mode or "proto tcp6-client" in TCP mode proto udp script-security 2 comp-lzo reneg-sec 0 cipher AES-256-CBC auth SHA512 auth-user-pass client-cert-not-required -----BEGIN CERTIFICATE----- [YOUR CERTIFICATE WILL BE HERE. LEAVE THIS ALL AS DEFAULT] -----END CERTIFICATE-----
- Save the configuration file and add it to any devices that you’d like to test the VPN connection with. I normally test the connection with my cellphone, as you cannot be on the same network as your VPN server. You MUST be testing this from an external network (cell phone/hotspot is a great option).
Step 5: Connect to the OpenVPN Server on an External Network
Now that we have configured everything for OpenVPN on a Synology NAS, we need to test our connection. Download the OpenVPN client on your cell phone or on a PC that you can connect to a different network. Remember, you must be connected to a different network to test this.
- Download the OpenVPN client software for your device here.
- Select the add button at the bottom and then choose File. You should now be prompted to browse for the .ovpn file that we created earlier. Upload the file and then login with your DSM username and password.
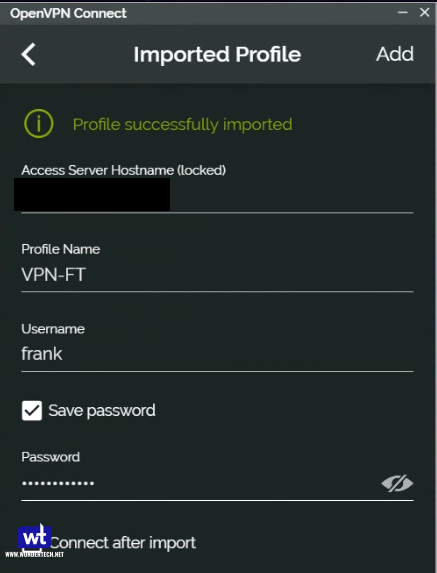
- You should be able to connect to your VPN now.
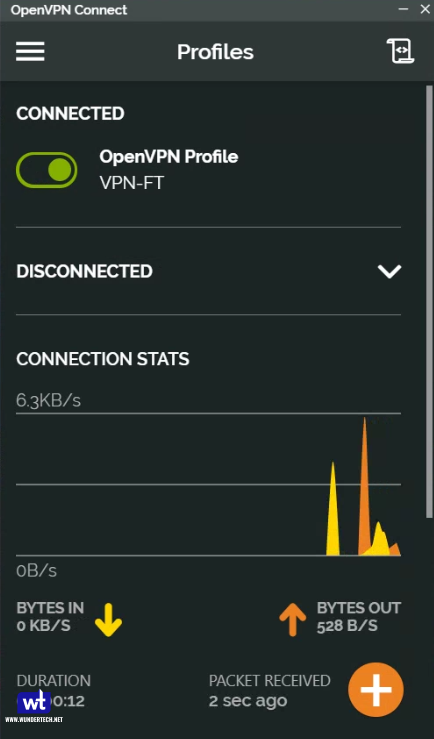
- I am going to show two examples below. First, I am connected to my VPN Server using my split tunnel connection. You can see that my external IP address is my mobile network (as I am accessing an external webpage).
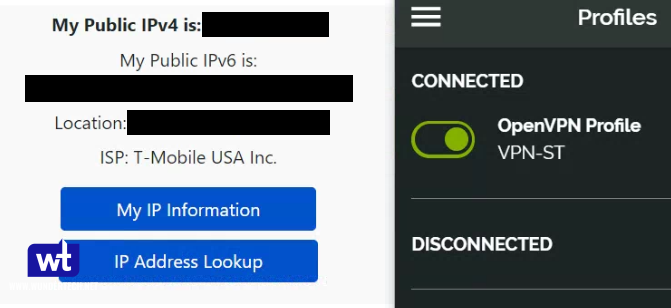
- In this screenshot, I am connected to my VPN Server using my full-tunnel connection. My external IP address is my ISP’s, as all traffic is being routed through my home network.
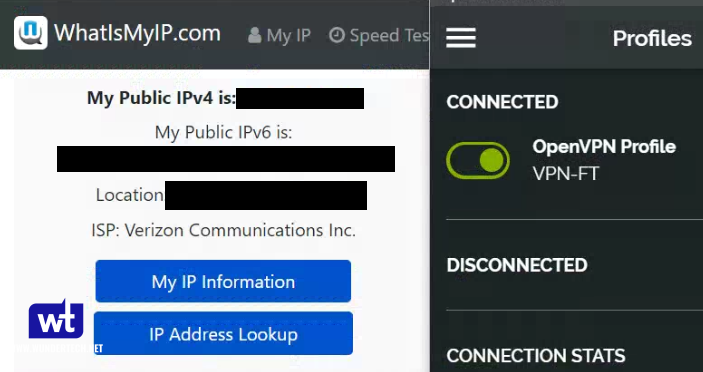
Both, split tunnel and full tunnel VPN connections allow you to access your local resources when using OpenVPN on a Synology NAS, but full tunnel VPN connections should be used if you’re trying to secure your network traffic (like when you’re on public Wi-Fi).
Step 6: Configure a Static Route for VPN Device Access
This step is not required unless you need to access VPN devices from your home network.
Your home network and VPN network will be on different subnets which means that your local devices will only be able to talk to the machines on its subnet (VPN network will see both).
In order to have your local network talk to your VPN network (in my case, 192.168.1.X and 10.5.0.X), a static route will need to be configured in your router. I cannot go over the setup steps for this as each router is different, but below is a screenshot of the static route that I configured.
The Gateway IP Address will be the IP address of your Synology NAS (since that’s where your VPN is running). The 10.5.0.0/24 subnet is where you will need to enter the IP range you are using (as defined in the OpenVPN settings).

Conclusion & Final Thoughts
This tutorial looked at how to set up OpenVPN on a Synology NAS. Configuring Synology’s OpenVPN Server allows you to securely connect to your home network to access your NAS and local resources.
It also completely bypasses the need for QuickConnect or exposing your NAS to the internet (which is a security risk). As an added benefit, the full tunnel VPN connection will also secure your connection when on public Wi-Fi devices!
Thanks for checking out the tutorial on how to set up OpenVPN on a Synology NAS! If you have any questions, please leave them in the comments!





Thank you for this. It is appreciated! Worked out great!
Awesome tutorial. Just had 1 issue, had to add the dynamic ip address range from the VPN server to a firewall rule. Otherwise it would connect, but I wouldn’t get internet access even though allow lan access is enabled. Not sure what I missed. Great guide tho!
That’s interesting. I didn’t run into any issues like that, but I appreciate you sharing for future visitors!
Hi Alex, can you post an example of what you had to do to get the full tunnel working, I have exactly the same problem.
Can confirm that I had the same problem! I added the rule to the firewall and now everything works ok!
What exactly does Step 7 here do? I followed these instructions and was able to get the VPN working. However, I noticed that if I want to navigate to my NAS from windows explorer, I have to go to “\\192.168.1.2” (my NAS’ IP), instead of being able to use “\\DS920” (the name of my NAS). Also, none of the other devices in my local network show up under Networks when connected to the VPN outside of the local network. Is this what Step 7 is meant to fix?
Thanks for following the tutorial!
Step 7 is a static route setup. Which basically says that devices on your local network can connect to your VPN network (ex: local PC needs to connect to your phone). This isn’t very common and most people don’t need this. It’s really only necessary if you have an off-site backup server that you need to connect to or something similar.
The issue that you are running into is DNS related. DNS stands for domain name system, which is kind of like a phone book for IP addresses. When you connect to your NAS’s name (DS920 in your case), your DNS server will look up that name and find the IP address associated with it. Without knowing the DNS server to use, you will not be able to connect to DS920, but you WILL be able to connect to the IP address.
You have two options: you can setup a DNS server (Pi-hole is a great option), but this means implementing a new system. Second option is to reconfigure your OpenVPN config file to enable split-tunnel DNS. I will do my best to explain it below, but feel free to ask any follow-up questions you might have.
1. Open a windows command prompt and type in the command “ipconfig /all”. Note down the “Connection-specific DNS Suffix”, as well as the “Default Gateway”.
2. Edit the OpenVPN config file that you have and add these three lines:
dhcp-option DNS [DEFAULT_GATEWAY (found above)]
dhcp-option DOMAIN [CONNECTION_SPECIFIC_DNS_SUFFIX (found above)]
dhcp-option DOMAIN-SEARCH [CONNECTION_SPECIFIC_DNS_SUFFIX (found above)]
You will end up with something like this:
dhcp-option DNS 192.168.1.1
dhcp-option DOMAIN home-router.home
dhcp-option DOMAIN-SEARCH home-router.home
Upload that new config file to your VPN device and retry. You should now be able to resolve the NAS by its name. If you have any issues, feel free to follow up. Thanks again for reading!
Good tutorial, but just like Alex on 04th September I can’t get the full tunnel option to work. I can access my NAS but not the internet. The split tunnel option works fine.
Are you using an iPhone/Mac to test by any chance? In iOS 7.0+ and MacOS, you need to add this line to the config file as well to get full-tunnel to work.
redirect-gateway ipv6
Let me know if this doesn’t work and I can try and help troubleshoot.
No, I’m using OpenVPN on Android. I’ve tried various things like turning off ipv6 and changing dns server details in various places (as when I try to open an external website it returns that the name could not be resolved) so thought that may be a DNS issue, but I might be grasping at straws. Any help would be much appreciated 🙂
Got it! A few things to check:
1. If you are using a local DNS server in the config file, can you change it to Google’s (8.8.8.8) and see if you are able to resolve domain names? It sounds like it can be DNS related, so you’re on the right track.
2. Another issue that I’ve run into in the past – by any chance, are you using Synology’s Firewall? If you are, can you disable the Firewall (only temporarily) and test to see if everything works?
I apologize for starting with such rudimentary troubleshooting steps, but since you’re connecting properly, it’s most likely something like this. Let me know how it goes!
Ok, I will try those, but before I do (and I’m sorry if this sounds like a dumb question but I’m new to world of all things NAS), am I ok to add the LetEncrypt certificate to my DDNS entry before I set the VPN back up? I’ve gone back to a pretty much fresh build of the NAS as I was changing so many things trying to get it to work, and just thought it easier than trying to revert back each of my individual changes (easier as there’s nothing saved to the NAS yet as it’s new).
Cheers,
Steven.
Never a dumb question!
Yes, you can add the Let’s Encrypt certificate before setting your VPN up. While you can change the certificate for your VPN Server in Synology’s settings, I’m not sure it’s actively used for OpenVPN. Since Synology only uses the .ovpn config file, I’m fairly certain that it bypasses this, which is why it’s not going to have any ill effects. Let me know if you have any questions and how it goes!
Ok, so I recreated the VPN connection, and with the Firewall left enabled it didn’t work, so as per your suggestion I disabled the Firewall, restarted the VPN and it started to work.
So I’m assuming I need to add something to the Firewall to get it to work when it’s enabled? I did add one or two things to the Firewall and got it to work when enabled, but not sure if I should be adding them, they were the application options under the Firewall for Webstation etc, (basically ports 80 and 443).
If it works with the firewall disabled, the most likely cause is that your VPN network is not allowed to connect to your NAS. Try and create the rule below and see if this works. It’s kind of hard to explain through text (without images), but hopefully this makes sense:
– Create an allow rule for all ports and the Source IP set as “specific IP”. Inside of that, select “Subnet”, and then enter the subnet of your VPN network. You can check the VPN Server package and OpenVPN for the “Dynamic IP address” (as this is your subnet), and then add your subnet in the firewall rule like this:
IP Address: 10.5.0.0 (replace the 10.5.0.X with what is entered in VPN Server. Keep the 0 where the X is)
Subnet mask/Prefix length: 255.255.255.0
Basically, replace the 10.5.0 above with whatever your VPN server is setup with. Add the firewall rule, put it above the deny rule, and see if that works. My suspicion is that it will, but let me know if it doesn’t and we can further troubleshoot. Sorry for pretty terrible instructions, it’s just somewhat hard to explain. Let me know how it goes!
Thanks a lot for the tip, I was struggling to get internet access through L2TP from my iphone. Opening all the port may not be a best security practice, I tried to select some with the application selection from the firewall configuration, but opening all ports seems the only viable option… any idea of wich port are required for outbound internet connection ?
I haven’t used L2TP, but when you say that you tried to open some of the ports, which ones did you try to open? According to Synology’s documentation, these ports need to be opened (UDP): 1701, 500, and 4500.
Let me know if that works and if it doesn’t, we can continue troubleshooting!
Sorry, I was not very clear 🙂 …. I managed to connect from my Iphone to my Synology throught L2TP VPN protocol. Once connected, I managed to get access to my Synology resources BUT without access to Internet. Thanks to your post, I allowed all VPN assigned IP to ALL ports and with this configuration I have access to internet throught the VPN connection. I was simply wondering if we can limits to specific ports, I tried multiple one (HTTP/L2TP/…) but without success, only all ports open allow me to get this internet access.
Thank you.
Hmm, if I had to take a guess, I’d say port 53. Port 53 is used for DNS, so it was probably working as expected but was unable to resolve domain names since port 53 was closed. Opening “all” ports freed up port 53 which allowed DNS resolution and internet traffic worked properly.
Try and narrow it down to port 53 only and let me know if that works!
Thanks for the video and written tutorial! Though the comments section was the one that helped me to succeed (Your 10 SEP 2020 comment)!
Synology NAS firewall (as set up in the tutorial) prevents me to access internet, 192.168.1.254 (router LAN address), 192.168.1.150 (NAS LAN address) and \\192.168.1.150\home (SMB share via Windows Explorer) over the full-tunnel VPN (disabling firewall everything works)!
[1.] Why did’nt You put this additional rule (All All 10.X.0.0/255.255.255.0 Allow) into the tutorial?
Wanted to be more specific (than All All 10.X.0.0/255.255.255.0 Allow) in the firewall rules {[2.] though I wonder if beeing more specific provides any security benefits?} and found out that:
5001 TCP 10.X.0.0/255.255.255.0 Allow – gives access to NAS LAN address;
137,138,139,445 All 10.X.0.0/255.255.255.0 Allow – gives access to SMB share.
[3.] Unfortunately I can’t find a rule to allow for internet and router LAN address access!?
PS. The “Conclusion” paragraph got me a bit confused.. What did You mean with “technically you are exposed ot a man-in-the-middle attack” (could You explain a bit more)? How running OpenVPN on Raspberry Pi or router would improve the security? What about configuring the server/client certificates ([4] isn’t it possible on Synology too)?
Best regards!
Overall, the Synology implementation of OpenVPN is poor. That’s not to say that there’s an inherent risk in running it (I run it), but it is to say that you should be aware of it. This link will explain it in greater detail: https://community.synology.com/enu/forum/17/post/113967
You can fix it by doing an outside process (documented somewhere in a different language), but running it on a Pi doesn’t contain the same vulnerabilities that Synology’s implementation does. Overall, you’ll have to determine what your risk tolerances are and go from there. Another great option is running WireGuard on a Raspberry Pi.
Sir, you are an absolute star, that worked a treat first time. The instructions were really easy to follow and not terrible at all, so no need to apologise for them. Big thumbs up from me.
I now look forward to trying your Bitwarden tutorial 🙂
That’s awesome, I’m glad to hear it worked! Good luck with Bitwarden – if you need any help, let me know!
I have bit of a further update on this. After watching one of your recent videos on Firewalls I decided to do a bit more digging to secure things up a bit more. I’ve narrowed down the exact port required to be opened t(o the VPN IP addresses) to be Port 53, and after doing a quick search this looks to be the port used by the NAS for DNS as per this page:-
https://www.synology.com/en-global/knowledgebase/DSM/help/DNSServer/dns_server_desc
Hope this is of help to anyone else. But again, many thanks to WunderTech for pointing me in the right direction initially.
This is very helpful – thanks a lot for sharing! Glad to hear it’s fixed and if you need anything else, please let me know!
Thanks for posting this great step by step tutorial. I have tried many others, unsuccessfully, while setting up my NAS to allow others VPN access for our fledgling business, but you covered everything. We now have others accessing the NAS for data storage and transfer.
A quirk has appeared though. After a couple of weeks of not directly accessing the NAS (direct IP address or Synology Assistant), neither of these will work now. The Assistant can no longer find the NAS and the direct IP address (still visible on the router), will not connect. I did shut off the router firewall for a moment to see if that restored access, but no luck. Any thoughts?
Glad to hear that it was working! Hope we can get it resolved.
When you say that it stopped working, do you mean through the VPN? Meaning that devices that were connected via OpenVPN could not access the NAS? Or do you mean that devices on the local network could not access the NAS? Also, is it not working for a specific service, or can you not access anything (DSM, file shares, etc)?
Let me know and we can continue troubleshooting! Thank you for checking out the tutorial!
Thanks for the reply. VPN access from outside works fine, I had just lost direct access to the NAS from my ethernet connection. Using the same PC that was used to set everything up, and while someone outside was accessing the NAS through the VPN, my Synology Assistant is unable to find the NAS (but could during setup) and I could not access it via the 192.168.0.nnn.
I have regained access this morning though! For others who may be running into the same issue, I needed to use 192.168.0.nnn:nnnn to log in.
The Synology Assistant still cannot locate the NAS, even when I have logged in via IP address. Interesting to say the least.
That’s definitely a strange issue but I’m glad to hear that you got it worked out! If I can help with anything else, please let me know!
Hi there, with Synology with 2 LAN Ports and different IP-Adress, shouldn’t it be possible to assign one of them to Pi-Hole only?
I haven’t tried it, but I’m not sure that you can do it either way. When you use both LAN ports, DSM recognizes both of them. You’d in essence have to pass through the LAN port directly to docker (bypassing DSM) and I don’t think that’s possible.
I might be overlooking something, but that’s how I understand it. Hope that helps, but if I can answer anything else, please let me know!
Hi!
Short question, i have a static IP adress from my internet provider. At step 5 “Synology NAS OpenVPN Configuration File Changes”
YOUR_SERVER_IP do i have to just put in the external IP adress from my router?
Thanks!
You are correct! If you have a static IP, you can add that there. Most people have dynamic IP addresses so they normally have to setup DDNS, but since yours is static, you’re good!
If you need anything else, please let me know! Thanks for checking out the tutorial!
When I try to enable OpenVPN from the nas I get this message (To talk about the OpenVPN service, you must first import the intermediate certificate corresponding). I’ve made a let’s Encrypt certificate. No change.
When you say that you get that when you try an enable it, do you mean when you try and check off “Enable OpenVPN Server”? If you go to the Certificate section in Control Panel and select “configure”, is a certificate assigned to the VPN Server?
Let me know and we can continue troubleshooting!
Hi, thanks for the guide! I’ve also hit the same issue, and do have a custom Let’s Encrypt certificate assigned to the VPN server in the Configure section of the Certificates.
What else could I be missing?
Thanks!
I haven’t seen this error in specific. Do you think that you can give me a little more background? When the error occurs, how it occurs, etc?
Let me know and we can continue troubleshooting!
I had a quick play around, and found out that when configuring certificates, if I remove my custom Let’s Encrypt certificate, and move the VPN Server service certificate to the synology certificate, I am able to enable the OpenVPN connection. However not too sure why this is the case, and what is wrong with my custom certificiate.
That partially makes sense. By any chance, did you export the OpenVPN config file before changing the certificate? If you did, you might have to export the configuration file AFTER setting the LE to be the VPN server’s default configuration.
Keep in mind that it might be best to leave it as Synology, as LE certificates expire after three months and might cause you issues when they do. Let me know if I can help at all!
Hi,
First thanks a lot for the tutorial. It’s by far the best one stop solution to figure out VPN setup which I’ve seen so far.
I’ve one question. I followed the tutorial to the T but I’m unable to access my NAS using FQDN I used for DDNS service on port 5000/5001
Similarly, I can see using nslookup and OpenVpn android app that DNS lookup is successful. So I’m assuming that the DDNS is doing its job.
I’ve setup port forwarding in my router but still no luck.
Final observation, I can at least access using my NAS on port 5001 when I’m on the same network.
What else I’m missing here.
I’m glad to hear that it helped! A few questions that I am hoping we can use to narrow down what the issue is.
1. When you say FQDN, are you talking about the DDNS hostname you set up with Synology (x.synology.me)?
2. Do you have a local DNS record for that DDNS hostname? (x.synology.me mapped to the IP address of your NAS)
My initial thoughts are that if you are using the synology.me hostname, that will point to your external IP address rather than the NAS’s internal IP address. You would need a local DNS record to ensure that FQDN is sent to the correct internal IP. Let me know and we can continue troubleshooting!
Hi – Great guide
I’m sctually having trouble with Step 2. When I try to create the openVPN profile, I get an error message that says” To enable OpenVPN service, please import the corresponding intermediate certificate first”.
So you know what this means and why this might be happening to my system? Thanks
The only thought that comes to my head is that you don’t have a certificate assigned. When you go to the Control Panel -> Security -> Certificates -> Configure, do you have a certificate assigned to VPN Server? If you don’t, you will have to add one.
Let me know and we can continue troubleshooting!
Hi, I truly appreciate the easy to follow guide here
As a follow up to the set up process on Step 7, I can’t seem to be able to ping my client (192.168.2.X) devices through the local network (192.168.1.X). My Synology is sitting behind a router which had port forwarding set up. The router I’m using is an Asus router, on its configuration page for static route. I should set the Network/Host IP to the IP that OpenVPN will assign my clients, netmask to be 255.255.255.0 then the gateway to be the IP address of the Synology, correct? There is an extra options here on the Asus configuration page which are Metric and Interface. I left the Metric as empty and left the interface to be LAN.
With all that’s said, I’m still unable to ping any client devices through my local network. Could I get your assistance on this?
You are correct, you need to set up a static route but it looks like you set everything up correctly. It should look something like this:
192.168.2.0 (I am assuming these are the IP addresses OpenVPN will be handing out. If not, use the OpenVPN IP Address range XXX.XXX.X.0).
255.255.255.0
IP Address of your Synology NAS.
I can’t comment on the metric or interface, but default should be fine. By any chance, do you have multiple NIC’s for your Synology NAS? If you do, can you try using the other IP address for your Synology NAS? A reboot is sometimes required as well.
Let me know and we can continue troubleshooting!
Hi Rob, Did you get this solved. I’m in the same boat as you. The client router can ping the host router and NAS but the host router cannot ping the client so I wonder if my static route is setup correctly.
Cheers
Not sure if Rob will reply, but after you set up your static route, did you reboot your NAS? I needed to do that initially when I set up my static route.
Love your website and YouTube Channel.
I’m stuck on trying to get VPN to connect. I’m fairly positive I’ve followed the instructions to the T, but I cannot figure out why, when I try to connect to VPN, the connection is timing out in the OpenVPN client.
I click the little log file icon to see what Open VPN is reporting and it jus shows that the connection is timing out. It is showing my Public IP for my ISP in the log, so that’s good, but it’s not making it further than there.
I’m trying this while using external internet, per the instructions. I’m tried temporarily disabling Firewall on both my router and the firewal for the Synology, with no luck. I must be missing something, but i’m stumped.
Thanks so much!
First, let’s check to ensure UDP port 1194 is opened to the outside internet. If you can, please select “Advance” in the link below, enable “UDP Scan” and change the “Start Port” and “End Port” to 1194. If you scan, do you see that 1194/udp is open?
https://www.ipfingerprints.com/portscan.php
Let’s start there and if it’s opened, we will move on to further troubleshooting!
Awesome tutorial! I read through the comments and I saw that there was a guy having issues with accessing some apps running on the NAS when firewall was enabled. I have this same issue. Anyway I took your advice and added a new rule which basically opens all ports using the vpn dynamic ip address as the subnet. This works well but having to open all ports does not seem to be the best solution. Do you know why this is a problem to start with? I thought that having VPN enabled would make it seem like my device was on LAN just like the other devices but something is different because when I actually am on LAN, I can access the apps with the firewall enabled.
I saw that you mentioned port 53 which I enabled but that did not help. Any ideas? I have the same problem on both full or split tunnel.
Thanks again!
I just realized, could this have to do with the fact that the ip-addresses the vpn connected devices get is not the one of the ip-addresses that the devices that are actually on LAN get? Because in my firewall I have a rule that allows all devices on my subnet.
Something like 192.168.1.1 and then 255.255.255.0 as subnet mask. I guess the internal devices connected through VPN gets another internal ip address?
The reason this is an issue is because the VPN subnet is different than the local network’s subnet. Generally, it comes down to one specific port needing to be opened and that’s the issue.
A few things to check:
You said you have 192.168.1.1/255.255.255.0 – This should actually be 192.168.1.0/255.255.255.0. Can you please try that and let me know if anything changes?
If you create a new rule for the IP address of your VPN subnet (default is 10.8.0.0/255.255.255.0 I believe, but I could be wrong), does it work? If it does, can you try and narrow it down to port 1194/53 and see if it works?
Let me know how it goes and we can continue troubleshooting!
I Understand! Thanks for the reply. I changed from 192.168.1.1 to 192.168.1.0 which did not make any difference. On the VPN subnet I have 10.8.0.1 not 10.8.0.0. When looking on the VPN server it says dynamic address 10.8.0 then there is a 1 at the end which I can’t change. I tried with 10.8.0.0. and allowed both 1194 and 53 but that did not make any difference. I am trying to reach NASIP:7878 which is a docker container. This only works when I allow 7878 in the VPN subnet. But yea it would be nice to not having to open all ports :).
I mean 1194 is already allowed through a rule where I selected from a list of built in applications where I chose VPN Server OpenVPN.
I replied but it seems like my response disappeared, I’ll try again.
I changed 192.168.1.1 -> 192.168.1.0 which did not make any difference.
In VPN Server under OpenVPN the dynamic address is 10.8.0.1 where I can’t change the last number (1).
I tried both 53 and 1194 although I think 1194 were already allowed because I have a rule where I have enabled VPN server (OpenVPN) through the list of built in applications. Neither solution worked.
I am trying to access port 7878, so basically IPNAS:7878 during VPN but it does not work unless I either allow 7878 in the firewall or all ports. Maybe I do have to allow each port that I want to access because the VPN subnet is different then the local networks subnet?
You are correct! If you have a firewall rule and only allow one subnet, you will have to create one for both subnets. As long as the port isn’t opened on your router, there’s nothing wrong with keeping the port opened for “all” and only having one rule.
Let me know if you have any other questions!
Hey!
I got a question regarding split tunnel. When I am on mobile data I can access my apps with
localNASip:port for example 192.168.1.25:3000 when I activate split tunnel and full tunnel. However, if I connect to my parents wifi it does not work with split tunnel. Full tunnel still works but not split. Could it be that it is trying to find the ip adress on my parents LAN or what could be the problem?
Hmm, that’s strange. When you say it does not work, do you mean that you can’t access resources on the local LAN or the outside internet? My assumption would be the local LAN but if it’s the internet, it could be DNS related. Let me know and I will try and help out!
Its the resources on MY local lan. So basically when I activate split tunnel I cant access my docker applications on my synology with the ip address and port. This is only when I connect to another wifi that is not my LAN. It works on mobile data.
Also I did add my router as the dns server in order to be able to access my synology with server name and port instead of ip address and port but this does not work all the time. It is very inclnsistent, sometimes when I am on my on wifi (LAN) I still cant access with servernname and port with vpn off. Sometimes it works sometimes it does not (iphone).
Can you access ANY services on your LAN, or is it only Docker containers on your NAS that you can’t access? Also, are you using a macvlan network interface for any of those services? If you are, can you try and use the bridge network IP address and see if you can access them?
As for DNS, do you have it setup like below in your OpenVPN config file? OpenVPN is fairly finicky and while it might work sometimes, you might run into issues if you don’t specify the exact domain (replace the IP address with your router and the example.com with your DNS server name (can be found using nslookup from a command prompt)).
dhcp-option DNS 192.168.1.1
dhcp-option DOMAIN example.com
dhcp-option DOMAIN-SEARCH example.com
I actually had specified the dhcp-option DNS 192.168.1.1 in my file but not the other two. I tried to find the DOMAIN and DOMAIN-SEARCH but CONNECTION_SPECIFIC_DNS_SUFFIX are empty if I run ipconfig /all. I can’t seem to find what to type in for:
dhcp-option DOMAIN example.com
dhcp-option DOMAIN-SEARCH example.com
Is there another way to find this DNS server name? I have both a windows and a mac that I can use to check DNS but not sure how to get the DNS server name
This is how you can find it on Windows 10:
1. Type Computer
2. Right click Computer from the results
3. Click Properties
4. You should see the fully qualified domain name next to the “full computer name”.
Let me know how it goes!
I could not reply to the latest comment. I followed your steps on windows 10 but I could not find anything there. I only found device name which is the name of my computer name. After that i only see the processor etc. Not sure I got the window you expected. Is there an image or so you can link to or a guide?
I tried nslookup in the cmd and all i get is the “default server” which is the name of my router basically: RT-AC86U-D460 and then the address which is the IP address of my router.
First off, I apologize. While we were doing something that could potentially help DNS resolution, I was making the wrong suggestion. I think I misunderstood your initial question and when I went back with a fresh head, I now understand what you’re asking.
In summary, when you’re on your parents Wi-Fi, their subnet being the same is a problem. The device doesn’t know what to transfer through the tunnel since you’re using the same subnet. When you are using the full-tunnel connection, ALL traffic is routed through the VPN tunnel which is why it’s working. In my research, there is a solution, but it’s not pretty. While painful, my suggestion would probably be to use the full-tunnel VPN when you have to connect back to your local resources. If you need to stay connected and it’s hurting your performance, this page has a solution that should work: https://serverfault.com/questions/548888/connecting-to-a-remote-server-through-a-vpn-when-the-local-network-subnet-addres
Once again, I apologize for the initial misunderstanding. If there’s anything I can do to assist, please let me know!
Hi wundertech,
i’m totally unable to get this working, i still get connected with my cell phone (android), but i cant access anything (neither local network, nor internet) :
– I tried to change every single option from within the .ovpn profile, without success, i tried to change UDP for TCP connection too (server and client), i changed dhcp-option DNS DNS_IP_ADDRESS (is there any matter for this option if i only want to reach the other local lan ?) and the redirect-gateway def1 (with and without), no success
– “Allow LAN access for clients” is check in DSM
– Openvpn Port (1195 for me) is correctly forwarded to the nas through my internet box, and is open in the nas firewall (i tried from all source)
– The Synology user (named vpn for me) got access and the correct permission for vpn server application in the nas
– i changed 3 times the password of that synology user
– i made a route to the vpn network into my internet box (gateway is the nas)
– i tried to make a route too from the nas to the internet box router
I still see the client connected through the vpn server panel of DSM (my cell phone got a right private IP address 10.10.0.6, and same in the android application, but i cant access anything on the other lan 192.168.1.0, handshake seems to be good (about 2 kb)
when i tried some basic based ip url when im connected (192.168.1.1 eg, is my internet box just for test), its searching for something, last a long time and then fail with “Time delay exceeded” error
what it could be ?
I would try and revert everything back to what it was initially. The good thing is that when everything isn’t working, it’s a little easier to figure out what the problem is. Do you have Synology’s Firewall enabled by any chance? If you do, can you try temporarily disabling it and seeing if it works? It sounds like a firewall issue since you are connected but can’t access anything after you connect.
Let me know if you do and we can continue troubleshooting!
Hi wundertech,
Thx for the answer, i finallly got an old rpi2 and i recycle it into a wireguard server at home, pretty much simple way with less configuration
WunderTech,
Great tutorials – both this one, and the initial setup. I learned some things, and I was able to make my NAS a little more secure – I greatly appreciate it.
I am having an issue that relentless troubleshooting and the internet hasn’t been able to help me with: I have set up an OpenVPN on my laptop and my parent’s computers to be able to access the NAS (they live overseas). Unfortunately, it only allows access to the DSM – I cannot map the NAS or see the NAS in Network.
Any ideas on how to fix this? Thanks in advance.
Thanks so much! If you’re able to see the NAS, I’d say that’s a good thing. A few questions:
1. Did you enable “Allow clients to access server’s LAN”?
2. Do you have a firewall setup on your NAS? If you do, can you temporarily disable it, test to see if it works and then reenable it?
Let me know how it goes and we can continue troubleshooting!
Hiya Wondertech!
I do have “Allow clients to access server’s LAN” enabled. I disabled my firewall and went looking for the NAS to pop up in “My Network Places” and no joy. I still have access through my web browser, but that’s about it. I don’t think it’s a firewall issue on my router side, since I have access to the DSM and I’ve tried on two separate networks (my wifi at another house and my phone’s wifi hotspot). It might be some adapter setting or a setting within the Network and Sharing Center, but I’m honestly not sure.
Thanks again! Great help so far!
Not a problem! Can you access them using their IP address? In looking over your issue again, as far as I know, “My Network Places” will not show devices on the destination server (your local network) by default. However, you WILL be able to connect to them by IP address.
If you have SMB enabled on your NAS (and the port allowed on the Synology firewall), open a “Run” command in windows and type the following:
\\YOUR_SYNOLOGY_NAS_IP
You should be brought to all of your shared folders (after authenticating). If you are, you can right-click them and “Map” them so they show on your parents PC.
Let me know how it goes!
WunderTech,
It worked! Thanks again, by far the best help I’ve gotten.
Awesome! Glad to hear it worked!
Thanks for the great tutorial! I got OpenVPN Full and Split tunnels working fine. I’m new to VPN and am probably making a noob mistake, but I can’t seem to figure out the following. I have a LE-issued SSL certificate installed for my (Synology) domain name, which works like a charm when I set up port forwarding to the NAS for the HTTPS port on my router. However, I don’t want to expose the NAS to the internet like this – so I delete the port forwarding for HTTPS and set up VPN Server. I can no longer get secure access to DSM on the LAN (which isn’t a big deal I guess), but when I connect the VPN and access DSM with the OpenVPN Dynamic IP, Chrome iOS generates privacy warnings – the certificate doesn’t seem to work, which does concern me – but should it? Connecting to DSM through the VPN using the domain name the certificate is issued for isn’t possible either. How can I access DSM through the VPN using a certificate-secured connection? Thanks in advance for your help! 🙂
Thanks for checking out the tutorial! The short answer is no, it shouldn’t concern you. A certificate basically confirms the website that you’re navigating to is who they say they are. On external networks, this is incredibly important and you shouldn’t navigate to any sites where they DON’T have a valid certificate. Internally, you don’t have to worry about that, as you know that you’re connecting to the right server. If you use the HTTPS port (5001 by default), your traffic IS encrypted, it’s just not verified by a certificate.
You can get around this by using self-signed certificates or implementing a local DNS server, but it’s slightly overkill and is really only needed if the Chrome privacy warning annoys you. It won’t provide any functional difference.
Let me know if I can answer anything else!
Happy new year and thanks a lot! 🙂
Thank you! Happy New Year to you too!
Hi Frank, I do have another 2 questions. I followed another of your great tutorials to install Bitwarden locally on my Synology. Thanks to your article, installing was a breeze and it works as expected. Just like in the above example (HTTPS), I have to forward another port in my router for Bitwarden (5554 in your example), which automatically allows external access using example.com:port (if I understand correctly).
1) I would rather have DSM and Bitwarden to ONLY be available from outside my LAN once the VPN has been established. Is that possible, and if yes, how should I achieve it – or would you advise against it?
2) When on the LAN, I also seem to require the port forwarding rules in my router in order to be able to reach Bitwarden or DNS using example.com:port from my browser. Could you point my in the right direction to fix this for local access without activating the port forwarding rules on the router?
Thanks a lot in advance!!
The short answer is that yes, you can do it, but it’s not as straight forward as you’d think. The bitwarden_rs container only exposes port 80 by default which is the HTTP port. The overall suggestion is to use a reverse proxy to get HTTPS to work, which also opens you up to using Let’s Encrypt. This is how the tutorial is written, but like you said, it exposes Bitwarden to the world.
If you want to access it when connected to your VPN only, you have three main options:
1. Use the HTTP IP address, but traffic to and from the container will not be encrypted. If you trust your local network, this option should be fine. Enable 2FA in all situations to keep the account secure. If you don’t trust your local network (shared internet, a lot of guests, etc.), I probably wouldn’t use this option.
2. Enable HTTPS using the documentation that the creator of the container published: https://github.com/dani-garcia/bitwarden_rs/wiki/Enabling-HTTPS
3. Keep the reverse proxy on, but limit traffic using Synology’s firewall on port 5554 to your local subnet and VPN subnet ONLY. The port will have to stay open on your router, but it should only connect if it’s coming from one of those IP addresses. This will in essence keep everything working exactly as it is, but limit traffic to your local network only. Everyone else will be blocked.
Option 2 will require you to translate it into Synology terms (meaning you’d probably have to mount the certificates as a folder, etc), but it’s doable. To answer your second question, you will only be able to use the domain you setup on options 1 or 3 above. You can technically do it on option 2 as well, but you’d require a local DNS server.
I realize this is probably a little more complex than you were hoping, but if I can answer any other questions, please let me know!
Wow, thanks a lot for your comprehensive answer! 🙂 Will be playing around with this. Keep up the good work, highly appreciated!!
I was stuck setting up a VPN server on my ds418 play and your guide helped me get it working. Thanks heaps!
I’m using Google WiFi (router), pi-hole on a raspberry pi 3 (dhcp) and ds418 play (VPN server).
I’ve followed your guide, but it still wasn’t working. THen, I went through the comments and found your mention about disabling the Firewall and giving it a go. BINGO! It was just a matter of adding a rule allowing traffic from the VPN network and magic happened. 🙂
Thanks a lot!
Awesome news! I’m glad it helped, thanks for checking out the tutorial!
Hi,
Thanks for the guide again, I’m still trying to get this working, however using a static IPv6 address rather than DDNS and wondering if you have any ideas?
Steps I’ve done so far:
– Enabled IPv6 to get a static IP from the ISP (Hyperoptic) on my Router (Google Nest).
– Have a custom domain (`example.xyz`) where the IPv6 address is a AAAA record on Cloudflare (although I’m quite new to IPv6 and it seems that two different PC’s on my network have different ending 4 blocks if that makes sense), so not too sure if I’ve set the IP correctly here.
– Port forwarded 1194 from the NAS to the router, and opened the firewall on the NAS (only UDP).
– Enabled the OpenVPN service on the VPN Server.
– Exported the configuration and updated the REMOTE_IP to exactly `example.xyz`, and updated to `proto udp6`.
– Uploaded the configuration to my android phone and tried connecting while on another network however it doesn’t succeed.
Other questions as well:
– Do I need to `Enable Ipv6 Server mode` in the VPN Server settings?
– Do I need some kind of custom SSL certificate for secure communications on the VPN? When clicking the connect button on the phone, it pops up saying `Select Certificate` which sounds like it’s not trying to use a certificate…
I suppose at the moment my biggest issue is with IPv6, as I’m not exactly sure what to put in the AAAA record in Cloudflare, I think it’s something like xxxx:xxxx:xxxx::2 ?
Any advice would be very much appreciated!
Thanks 🙂
I unfortunately haven’t set up IPv6, so I can’t comment on the exact steps but I think you’re on the right track. You most likely have to enable IPv6 and after you do, update the configuration file. Do you have the firewall setup? If you do, temporarily disable it to see if that resolves the issue.
Generally, it should function similarly to IPv4, so it’s most likely a setting or a configuration file setting.
Ah fair enough. I do have the firewall setup and have tried disabling it, but nothing seems to have happened there. I’ll have a play around with the configuration, and if I get anywhere with it, will report back. Thanks 🙂
Hi Frank,
I followed along with the video, and I’m pretty sure I’ve got it working correctly, but I have a question: I have a couple of services on my Synology serving via a remote proxy like https://service.mydomain.com. One is a Docker container, and the other is DSM. In my router, I’m forwarding Port 80, 443, and 1194 to my Synology, and I can access these just like I’d expect. The problem is that I can access them whether I’m connected to the VPN or not, regardless of whether I’m on my network or not.
Is this the expected behavior, and if so, how can I have reverse proxy services that I can only access over the VPN? Thanks!
Hi Chris!
The reason that you can access these services both, remote and locally is because you have ports 80/443 opened and you’re using a reverse proxy server. Generally, people suggest using a VPN to connect to your home network, then connecting to the local service from there. However, you’re using what sounds like two technologies (reverse proxy, VPN) at the same time.
A reverse proxy will expose certain services outside of your local network. So when you have 80/443 opened and create a reverse proxy, that service is exposed to the entire world. The VPN appears to be set up and working properly.
If you DON’T want these services accessible by the entire world, you need to close ports 80/443, connect to your VPN and then connect to the service by using its internal IP address. If you want to use the service by domain name (https://service.mydomain.com), you would have to implement an internal DNS server which points that name to the internal IP address of the server.
This is a lot of information and might cause a little confusion, so please feel free to ask any follow-up questions you have!
Great tutorial, thank you! I now have a vpn up and running and learned a few things along the way.
Quick question, and sorry if someone else asked this already in the comments. I am using the openvpn iphone app like you suggested. Is it possible to always have the vpn connection open while on my home network? Or is this a security risk / bad practice?
It unfortunately won’t work on your local network. When you’re outside of your local network, you’re basically tunneling back to your local network which “secures” your connection. When you’re on your local network, enabling it either will not work, or it will “appear” like it’s enabled and the internet connection won’t work.
Basically, when you’re outside of your home, if you’d like to “secure” your connection or access local resources, enable it. If you’re at home, there’s no need to enable it!
Cool, thanks for the quick reply and help!
Worked like a charm, thank you for being detailed yet easy to follow 🙂
Anyone else gets openssl context CA not defined.
I followed you’re instructions not sure what went wrong. Trying to get to my ds920+ via android phone.
Thank you
Where exactly are you getting that error? Is it on the Android side or the Synology server side?
Thanks for the great tutorial. I got also the same error on my android phone. In NAS the connection is normal and apparently, everything works fine.
Can you explain a little further the issue that you’re experiencing?
Hi, thanks for the great tutorial. Unfortunately I’m getting the same error. Not just with Android but also with the windows OpenVPN Client (trying to connect from outside my network).
I set up the VPN Server and changed the config file as you did. I just let the pound sign for “redirect-gateway refl” in, since I wanted split tunnel VPN and also the dhcp-option is still commented out since I have no local DSN-Server.
Then I just got the Android VPN-Client, loaded the file and tried to connect. After a few seconds the following error message occurs:
“There was an error attempting to connect to the selected server. Error message: ssl_context_error: OpenSSLContext: CA not defined”.
And that’s it. Can’t go any further. What could be the problem here?
Thank’s a lot for support!
A few people have been reporting this exact issue and I haven’t experienced it. When you log in to DSM and check the certificates (Security > Certificates > Configuration), what is listed for VPN Server?
In my certificates section for VPN Server my standard certificate from synology.me is listed. It’s still valid and it’s the domain that I also put into the config file in the line
Did you change DSM to a different certificate or are they all using that default cert?
I’ve used different certificates over time. There’s one expired one (also synology.me that I don’t use anymore) in my list and a quick connect certificate (still valid, but only used for quick connect).
All other services use the valid one from synology.me (WebDAV Server, Synology Drive Server, OpenVPN).
Since I haven’t ever received this error, can you check this link and try and implement his solution? https://community.synology.com/enu/forum/17/post/102738?reply=343868
This was very helpful. I can connect with my Windows devices but I am running into an issue with my Mac when I try and connect via SMB it will say “There was a problem connecing to server “192.168.1.210” The server may not exist or it is unavailable at this time. Check the server name or IP address, check your network connection, and try again. I can see from the OpenVPN Connect app that I am connected and I see from the Synology DSM that I am connected, I just can’t navigate to the DSM from Finder. Any thoughts on what could be causing this?
Are you using your Synology NAS by name and not IP address? You might have some issues with your DNS configuration if you are.
Hi, your tutorial is great and i could easily follow along. Just one small problem: i would love to access my router via vpn, for now i can access my NAS without any problems (full and split), but i have no chance accessing my router (standard 192.168.188.1) with activated vpn, i only land on synology´s page: Webstation has been enabled (and so on)…. for my understanding very odd to type in the routers ip and land on a local synology page (: i tried setting a static route as described in step 7 but theres unfotunately no change. Any ideas? Thanks!
You shouldn’t have to do anything special to access your router’s page. Do you know if it’s blocking requests from different IP subnets? Can you access all other network resources? It could be a setting on the router itself.
Hi! First of all thanks for the tutorial
I’ve tried to configure it as you say, but it doesn’t seem to work, it seems that the option client-cert-not-required has been deprecated, and I’ve tried to use the new replacement instead but it ask me for a –server mode option too, what can I do?
When you say it doesn’t work, what exactly doesn’t work? The client-cert-not-required simply bypasses the error that appears, so it wouldn’t be that. Is it not connecting at all?
I get the following error trying to connect on a Windows client. The same config works on the android client
Fri Jun 18 17:55:17 2021 DEPRECATED OPTION: –client-cert-not-required, use –verify-client-cert instead
Options error: –client-cert-not-required and –verify-client-cert require –mode server
Use –help for more information.
I haven’t tried “–verify-client-cert” yet
Yes, I have to update the tutorial (sorry about that). If you use “–verify-client-cert none”, it should function the same!
Hey WunderTech, amazing tutorial and videos!
I am however having an issue with OpenVPN on my Synology NAS, as I cannot reach any internet page (besides google?!) once connected via full-tunnel… The client I use, Tunnelblick, throws a lot of warnings regarding DNS, so I assume that’s where the problem lies:
__
*Tunnelblick: NOTE: The DNS servers do not include any free public DNS servers known to Tunnelblick. This may cause DNS queries to fail or be intercepted or falsified even if they are directed through the VPN. Specify only known public DNS servers or DNS servers located on the VPN network to avoid such problems.
__
*Tunnelblick: Warning: DNS server address 172.20.**.* is not a public IP address and is not being routed through the VPN.
__
*Tunnelblick: Warning: DNS server address fe80::1 is not a public DNS server known to Tunnelblick and is not being routed through the VPN
__
I am not running a DNS server in my NAS.
I believe that my DNS are resolved by my ISP router, which is my gateway 192.168.0.1.
I have tried all day changing the OpenVPN-config.ovpn file, with the dhcp-option commented:
#dhcp-option DNS 192.168.0.1
and uncommented:
dhcp-option DNS 192.168.0.1
I’ve also tried adding some public DNS servers:
dhcp-option DNS 8.8.8.8
dhcp-option DNS 8.8.4.4
Nothing seems to work. Do you have any recommendation?
Thanks a lot!
Are you using Synology’s firewall? If you are, did you allow traffic to port 53 from your VPN subnet? It sounds like it might be a DNS issue, so that’s the first thing I’d try.
Hi WunderTech – Great article.
Have a Synology DS918+ and have had it setup behind a Router with an external static IP.
The Synology NAS sits on the internal network with LAN IP : 192.168.11.220
The OpenVPN Client port is changed to port 1695
The routers IP GW Address : 192.168.11.254
Port fowarding is enabled from external on 1695 to port forward internally to 192.168.11.220
The NAS can be accessed internally from any device on 192.168.11.0/24 to 192.168.11.220.
The NAS can also be accessed remotely via QuickConnect.
** WAS WORKING PERFECTLY – As follows **
All devices internally on the LAN work ok – including accessing shares.
DHCP server is done by the router. (Not the synology NAS)
The OpenVPN client has been configured and connects ok to the Synology OpenVPN Service and allocates an IP of : 10.0.8.6
So when a Win10 client connect remotely – all services direct to the Synology NAS are on IP 10.0.8.1
I can connect to network shares on the NAS direct via the Client VPN on the Windows 10 PC.
To access any 192.168.11.0/24 I added the following static route on the Windows 10 PC.
cmd.exe (run as admin)
route add 192.168.11.0/24 10.0.8.6
route print (Then showed the static route)
This worked magically for a couple of months.
Once a Windows 10 PC worked remotely with an Internet Connection, launched the OpenVPN client
Connected ok – and was able to access any resource remotely within the 192.168.11.0/24 network (LAN).
This was great for accessing local printers on the LAN, access to internal reources.
So network shares were mapped as s: \\192.168.11.220\shareddata
Print drivers were pointed direct to the printers IP Address within 192.168.11.x network.
** THE PROBLEM **
Then one day this stopped working when connecting remotely. Not able to access any resources remotely on the 192.168.11.0/24 network.
I have tried removing and re-adding the static route on the pc.
I haven’t tried anything on the Synology NAS yet?
I can now only access resources direct on the 10.0.8.1 (Synology NAS) when the OpenVPN client is connected.
Network drives are mapped direct to the \\10.0.8.1\sharename rather than the \\192.168.20.220\sharename
But I really need remote printing working again to any local printers when working across the OpenVPN.
Any pointers, suggestions welcome.
It sounds like you have everything configured properly. I wouldn’t think it’s a static route issue since static routes are created for the reverse (local network accessing the VPN devices). Are you using Synology’s firewall by any chance? Did you limit traffic to only local IP addresses?
What about pinging a device by IP address (VPN to local)? Any reply?
Thanks so much for this. It was so easy to set up and now I’m wondering why I didn’t do this long ago. A couple extra questions:
(1) Even though I added “client-cert-not-required” in the config file, my Android phone still pops up that question when I log on. Is there any other way to stop this pop-up, or how can I import the cert file(s) into the Android phone so it has them?
(2) Along the same lines, I installed OpenVPN client on my laptop but it requires the cert files. I installed both cert files that Synology provided by double-clicking on them, which appeared to install fine, but yet I still get this message and cannot log on.
Thanks again.
Thanks so much!
1. I am using that line on Android and it’s working properly, though it is deprecated at this point. You can try adding this line and see if it works: –verify-client-cert none
2. The cert is not required, which is why you might be running into issues. If you can, try and add the line above and then use that config file on your laptop. My assumption is that it will work, but let me know if it doesn’t.
Let me know if you need anything else!
Thank you for the amazing tutorial! I’m able to connect to the VPN and access the local network just fine – however, my VPN connection regularly drops (every 5-10 minutes or so). It immediately reconnects, but by then the network folders get dismounted (amongst other troubles). Any idea why this might be happening?
OpenVPN logs show this:
14:26:44.615 — Session invalidated: KEEPALIVE_TIMEOUT
14:26:44.617 — Client terminated, restarting in 2000 ms…
And Tunnelblick logs show this:
2021-04-26 02:10:05.139880 [mynas.theddns.me] Inactivity timeout (–ping-restart), restarting
I’ve tried both full and split tunnel configs, and the Synology firewall is disabled. My research keeps bringing me back to DNS issues but I’m not sure how to proceed.
If you enter this line to the OpenVPN config file, it should work properly!
keepalive 10 120
Basically, the connection is dropping due to inactivity. This should help!
Thanks for the quick reply! I tried adding the setting but it didn’t work unfortunately – still getting the same error. I did try different timeout parameters as well in hopes to find something optimal but no luck.
I have noticed it tends to happen more often when I’m actually using an interface on the local server. i.e. If I just leave the VPN connected and do nothing it might disconnect after 15-30 minutes, but if I’m clicking around in DSM after two minute I’ll notice the OpenVPN client suddenly shows a high number of “Bytes Out” but 0 “Bytes In”. After staying at 0 for 10-15 seconds or so, it’ll disconnect and reconnect. Rinse and repeat.
Really appreciate the help!
I think I’ve managed to fix it! Though I’m not sure I know enough about networking to understand why, to be honest. I noticed that my IP address was an IPv6 address, and on a hunch I though “Huh, every tutorial I found has an IPv4 address. Can’t hurt to try.” So I forced my Mac (client) to obtain an IPv4 address from the router instead and the VPN connection has been perfectly stable so far! It even fixed my L2TP/IPSec VPN issues! No idea why this works but it did. I will probably jump further down the rabbit hole to figure out a more elegant solution though, now that I (sort of) know what’s causing it. Thanks again for your help!
I wish I could give you a reason as to why it worked (other than it’s clearly IPv4 related), but that’s great news! Glad you got it working!
Wow, thanks for the great tutorial. I was able to connect fine to OpenVPN using my test cell phone, but had a similar problem where I then could not connect to the internet or local area IP’s. Added the following firewall Rule and BINGO! Thanks WunderTech for the help and Steven for asking a similar question.
“– Create an allow rule for all ports and the Source IP set as “specific IP”. Inside of that, select “Subnet”, and then enter the subnet of your VPN network. You can check the VPN Server package and OpenVPN for the “Dynamic IP address” (as this is your subnet), and then add your subnet in the firewall rule like this:
IP Address: 10.5.0.0 (replace the 10.5.0.X with what is entered in VPN Server. Keep the 0 where the X is)
Subnet mask/Prefix length: 255.255.255.0”
I’m glad that it helped! Thanks so much for mentioning what fixed your issue!
Thanks so much Wundertech! The firewall entry to allow all ports solved my issue of not being able to Remote Desktop (RDP) to my PC when I am using the NAS VPN from an external IP. This works for either OpenVPN or L2TP/IPSEC.
I also posted the solution here and mentioned this thread: https://community.synology.com/enu/forum/1/post/148015?page=1&sort=oldest
Thanks again
DD
Glad that you were able to get it working and thanks for letting me know!
Hi wundertech! great great job on this tutorial, I’m loving your site and guides on synology NAS. You have great teaching skills sir ! keep going !
Thanks so much! I’m glad that they help!
Hi
I have got to the Part of saving openVPN file and what I should enter?
What is age hostname? is it the ip of the nas or the Duck DNS name I just am having problems with last parts
Any help would be much appreciated
Kind regards
Mike
That would be the location where you want clients to connect to (your external IP address). So it would most likely be the DuckDNS hostname that you set up!
Thank you so do you mean like wundertechtutorials.duckdns.org or just the wundertechtutorials or https://wundertechtutorials.duckdns.org
is that what you meant ?
thank you for the help
it may have been easier for us idiots lol to have used some fake ip settings etc so we could have just filled links of which ones we use in the config vpn file
only other one is the dhcp-option is this the DNS server eg 192.192.1.1
It’s just I am trying this in uk with Mac and VMware and a sky router so all a little new.
Really do appreciate all the help you have given so far great work !!!
🙂
Kind regards
Mike
yourdomain.duckdns.org should be fine! I will take that into consideration in the future. Thanks so much for the feedback!
This is a great tutorial! And thanks for so generously helping people in the comments.
I’m hitting an issue where I’m able to connect to the VPN remotely, but then when I try to mount the NAS on Finder with `smb://192.168.1.3`, which is the local IP, Finder can’t connect.I don’t have Firewall enabled on my NAS, and I’m connected fine to the VPN on the device. Any idea where I should start troubleshooting here?
Thanks for the kind words!
When you say you’re able to connect, does that mean you’re able to connect to other local resources and the NAS is the only device you can’t connect to? What about on the NAS itself – does it show the client as connected?
Hi WunderTech, great help with this article.
I have an issue/question with the dhcp-option. I don’t have any raspberry pi to create a local DNS server, in order to be able to use the hostname instead of the ip address.
My question is: can the DNS Server app from the synology package center be configured as a local DNS server? I’ve been searching on the web for this, but wasn’t able to find.
Yes, it can! You will have to set it up (I don’t have a tutorial on it yet), and specify the NAS’s IP address as the DNS server, but it should do exactly what you’re looking for!
Hi WT,
Your instruction is very clear to follow and I’m finally able to setup my OpenVPN and connect to it. But I do encounter some questions/problems throughout the process.
1. I understand and tested out the “client-cert-not-required” setting, but my question is that when I leave it as “”, I get different output when connect on different platform. Why is that?
– On my Win7 PC with Windows OpenVPN GUI, I can connect but took a little longer for some reason.
– On my android device, it did shows the “Select Certificate” message but able to connect after selecting Continue. The connection took just a few seconds.
– On my iOS device, it didn’t shows the error message but instead just connect directly and also took just a few seconds.
2. Once I connected, I was having issue to actually access the shared folder no matter what I tried. In the end I have to setup port forwarding and enable firewall for Windows File Server in order to access it. The question is that, based on several other tutorials, they are able to access without going through these setting. Did I mess up somewhere?
3. In your tutorial, you are able to connect to DSM with local IP and port, but I can’t seems to do that even with my firewall and port forwarding setup already. However if I’m on the actual local network, I can access DSM with local IP just fine. What could be the reason behind it?
Hello!
1. The timing will be slightly different, so I wouldn’t worry too much if one is quicker than the other. As for the “client-cert-not-required” option, it’s now deprecated. I need to update the documentation (thanks for reminding me), but you can use this option instead:
–verify-client-cert none
2. You should NOT need to port forward anything to access the services. Are you connecting via IP address or hostname? Can you ping the other servers?
3. It would probably be a good idea to take a step back and make sure that you’re successfully connecting (check inside of the VPN Server application). It almost sounds like you’re not successfully connecting.
1. Thanks for the new option and just to confirm, you mean to type it as below right?
verify-client-cert none
2. I’m connection using my NAS local IP and mapped it like \\192.168.1.100\home. But I can’t seem to ping the server when connected with VPN.
3. I check in DSM under VPN Server app and able to show the connected device from different platform.
I tried look up in Google again and apparently someone mention to turn off DoS protection/block in router setting. I did that together with removing WFS port forwarding on router and firewall in DSM. Turns out these did the trick.
The connecting timing on my Win7 PC get significant boost compare to before and I can access mapped drive almost instantly. However, I still can’t get to ping my server or any remote client for some reason and not sure what in my DoS protection setting is causing the issue.
1. Yes, that is correct!
2. If you can’t ping the NAS, there is some sort of problem. Did you select the option to allow access to the LAN? Any firewall that could be blocking traffic?
3. If the device is connected, I’d look at the firewall and see if there are any rules blocking access from that subnet. If not, you’re going to have to try and isolate what could be blocking it (since you’re able to connect to the VPN).
You’re right about the firewall. Apparently it’s my Synology NAS firewall that is blocking the ICMP protocol. I can now ping any network devices without any issue.
The only problem now is that my Windows File Explorer is not showing any network devices on the VPN side, including my Synology NAS. Per Synology Support, seems like it’s not possible to show Synology NAS if through VPN connection. Not sure if this happen to you and if same on all other network devices as well?
Are you using network discovery for that? You should be able to access everything on the NAS. Are you able to connect via SMB?
Great tutorial, very thorough.
When I followed your instructions my Android devices can connect with my NAS just fine. However, my Windows 10 laptop using the same ovpn file cannot. The error log contains:
DEPRECATED OPTION: –client-cert-not-required, use –verify-client-cert instead
Options error: –client-cert-not-required and –verify-client-cert require –mode server
So I substituted:
verify-client-cert none
Which results in the same log entry. I’ve tried OpenVPN versions 2.4.6 and 2.5.2 with the same results
If I leave the option out altogether it connects but I get a Warning.
How should I proceed?
Thanks.
Are you able to proceed through the error and it works, or the error holds up connecting altogether? You aren’t on the same network as the VPN server, right? You need to make sure you’re testing from a network outside of your local network.
Correct, I’m not on the LAN. I’m using my phone as hotspot for the laptop to connect to the internet.
If I leave the ‘verify-client-cert none’ option in, I cannot connect and get the log entry posted above. But as I mentioned above, if I leave the option out altogether it connects but I get a Warning in the log file. The warning is as follows:
WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm
FWIW the OpenVPN server is on my Synology NAS from which I generated the .opvn file using the Synology’s certificate.
Thanks in advance for any advice.
This is really nothing other than an assumption, but I am suspecting that the command isn’t working because Synology hasn’t updated their OpenVPN package inside of VPN Server. That would explain why a “new” command isn’t being recognized. If “client-cert-not-required” doesn’t work and the new command doesn’t work either, it might just be worth clicking through the error. I do think that there’s a chance (maybe in DSM 7) that the application is updated to recognize that command, but that’s just a hope. I will try and do some testing at some point to see if I can get “verify-client-cert none” to work. I always used “client-cert-not-required” and it worked properly for me.
Great help. I had set up my VPN and it worked well, but I was looking for the configuration to access the VPN client (aka another remote NAS).
Found the solution what to put into my firewall here. Thanks!
Just one additional question: I am using L2TP/IPSec instead of OpenVPN, and the VPN-Client-NAS must reconnect every night due to IP change by the provider (no static IP there yet 🙁 ). After approx. 50 successful attempts this procedure fails, and I have to restart the IPSec server. Has anyone experienced similar issues?
I haven’t seen that error, though I don’t use L2TP/IPSec. I assume that you’re using DDNS so that it automatically gets the new IP address?
I am having the same experience. The log says: Options error: –verify-client-cert requires –mode server. The status says: Connecting to management interface failed. It also says: OpenVPN exited with error: exit code =1
If you remove that line entirely and click through the error, does it allow you to connect?
Yes, thanks!
Great instructions. I have a different setup. My ISP provided me a IPv6 DS Lite connection. Portforwarding router to NAS does not work anymore. What I did is a connection with my own domain using a VPS Server and 6tunnel. Any change to setup a VPN as well with this setup? Thanks again
I haven’t personally seen a way that you can get that working, but I’m sure that it’s technically possibly somehow. Though it wouldn’t be a traditional setup process/procedure since you’d have to try and form some connection between the VPS and your local network. You might have more luck trying to run this on a dedicated Linux machine since the NAS might limit your options. Again, just guesses unfortunately. Sorry for not being much help!
Thanks for the great video. I am having a 3 years Netgear Orbi RBK50 mesh router and strangely the “Advance Setup” disabled the “Port Forwarding/Port Triggering” and “VPN Service” function. Any idea why this is happening?
Unfortunately, I’m not familiar with that router. Is there any type of product that they have that might be closing them to try and “protect” you?
Just a comment on a setting I was stuck for a while: I was able to access my home network by IP but not any website by DNS. I was using Pi-Hole as DNS server and I had to turn on “Listen on all interfaces, permit all origins” on Pi-Hole settings / DNS configuration. Otherwise my requests over VPN were being ignored.
Thank you for sharing that! Very helpful!
Hi WunderTech, great tutorials! been followed your other tutorials as well.
I believe I followed all the steps and watched the video quite a few times, but unfortunately not able to get the openVPN work.
I tried to use my iphone’s celluar data as hotspot and connect from my pc to test it.
### 1. when test on Linux client:
“`
openvpn –config /path/to/VPNConfig.ovpn
WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
TCP/UDP: Preserving recently used remote address: [AF_INET]my.ip.address:1194
UDP link local (bound): [AF_INET][undef]:1194
UDP link remote: [AF_INET]my.ip.address:1194
TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
TLS Error: TLS handshake failed
SIGUSR1[soft,tls-error] received, process restarting
….keep repeating these messages ….
“`
note I have comment the “client-cert-not-required” line due to the “–server mode” error
### 2. when test on Win10 client:
after drag in the same .ovpn file, it pops a window for the certficate, I choose “continue”, then keep waiting, the log said:
Connecting to [my.ip.address]:1194 (my.ip.address) via UDPv4
EVENT: CONNECTION_TIMEOUT BYTES_OUT: 840 PACKETS_OUT: 60 CONNECTION_TIMEOUT:1 N_RECONNECT:5
then it keeps say “connection failed to establish withing given time”, “Retry / Cancel”
I tried to disable Firewall temporarily, not work. I also tried to turn on other related port forward than just 1194, also not work.
please advise?
The first thing to check would be to ensure that the port is opened properly. Can you check this website, enter in your external IP address and then port 1194 and confirm that it’s open? https://www.ipvoid.com/udp-port-scan/
Thank you, from the website you provided, it said:
Port Type Status Service
1194 UDP Open|filtered openvpn
some extra info if it could be helpful:
– I can connect to openVPN if I change the UDP to TCP protocol without a problem!
– I suspect it is a MTU issue, I have router port 1194 open to both UDP and TCP, then tried http://www.letmecheck.it/mtu-test.php with my Synology external IP; report:
Sending 32 bytes to nas.external.ip.address 1472 fails): ping -f 192.168.***.*** -l 1472
where 192.168.***.*** is my NAS internal IP address.
– also tried to test UDP connection from linux machine when connecting to my phone’s cellular network:
$:nc -vzu nas.external.ip.address 1194
Connection to nas.external.ip.address 1194 port [udp/openvpn] succeeded!
$:nc -vzu nas.external.ip.address 1234 #a random port
Connection to nas.external.ip.address 1234 port [udp/*] succeeded!
That’s interesting. So when you connect via TCP, does it work properly? Meaning can you access everything? Do you think there’s any chance your ISP is limiting traffic on UDP 1194?
I am not sure about the ISP and port restriction, and I feel it probably not a reason. I feel this is beyond my knowledge, and will accept the gently slower and less safe TCP for now and see whether further package update can solve this issue. Thank you for the great feedback! I will keep watching your channel! –Chui
Absolutely nothing wrong with using TCP, so I wouldn’t view it as downside. Glad you have it working!
I am not a techie. I do appreciate your tutorials because you guide a person well on how to set up the NAS. Question – what if I have a Static IP address? Do I still click apply Enable OpenVPN with the Dynamic IP address? If I am good with just using the dynamic IP am I ok with leaving the Port as 1194? I get a prompt asking me if I’m sure 1194 is available.
If we take a step back, when you say static IP address, do you mean static external IP address?
Thanks for writing this guide. I ran into a couple issues I was able to resolve including:
– Import intermediate certificate: I had renewed my SSL, but my DS was giving me an error saying I was missing the intermediate certificate. I had to re-import my certificate but making sure to include the intermediate certificate from Sectigo (ca-bundle file).
– Missing client certificate: Using OpenVPN Access 3 client on my Mac, I was getting an error saying that I needed a client certificate. There are 3 workarounds here:
1) Ignore this “Connection error – Missing external certificate” message and just click “Continue” instead of “Select certificate” every time you connect.
2) Edit your .opvn file to add “setenv CLIENT_CERT 0” and then it will stop asking you for a client certificate each time
3) Add a client certificate – I used instructions from the following Medium post and added the p12 certificate generated through easyrsa to Keychain access and it works beautifully! https://medium.com/aws-tips-and-tricks/aws-client-vpn-connect-using-openvpn-3c411100220a
Thanks so much for sharing this great info!
Hi, I would like to do a static routing, because I want to see vpn devices from local devices and vice versa. But the problem is I don’t have static routing option in my router. Can I do it in my NAS? It will be/should be the same? (the NAS running the VPN server)
I haven’t had experience with Synology’s Static Route feature and if I’m being honest, I don’t think that it will work. With that said, you can definitely try it – you can set up the static route in DSM (you might have to reboot) and see if it works.
I’m using a cloudflare origin certificate for ssl/tls certification. And It simply won’t let VPN Server to run at all, unless you change the vpn server’s certificate to a non-origin server certificate. Does anyone know why it simply does not work but keeps asking intermetiate certificate when we don’t have one at all?
I haven’t tried this, but I can imagine it would be a problem. The truth is, Synology’s implementation of OpenVPN is not the best. Do you want to use the origin certificate for VPN, or are you just trying to bypass it?
From VPN connect on cell phone, I get this error:
There was an error attempting to connect to the selected server. Error message:
OpenSSLContext:SSL read_cleartext BIO_read failed, cap-2576 status==1; error: 1416F086:SSL routines tls_process_server_certificate very failed
Can you suggest what steps I may be not implementing correctly?
I haven’t seen that error – can you confirm what certificate is assigned to OpenVPN in DSM?
I have the exact error message on my iPhone app (I’m using DS1517+)…
There was an error attempting to connect to the selected server.
Error message:
OpenSSLContext:SSL read_cleartext BIO_read failed, cap-2576 status=-1; error: 1416F086:SSL routines tls_process_server_certificate very failed
I’m not tech savvy at all, I’m not sure where I’ve gone wrong, but I really want OpenVPN installed so I can access my docker containers while away. Do I need to enable IPv6 within the VPN Server?
The only way I’ve managed to make it work is by configuring the VPN Server Certificate to synology.com, is this okay or safe?
Yes, that should be fine! Glad you got it working.
Thanks for responding so quickly. I am traveling out of town for about 2 weeks so I won’t be able to follow up for a bit. AFAIK, I just exported the certificate as you said and used that in the app. I only changed the one line to remote ****.DSmyNAS.com 1194
I used the tutorial to connect to my Clients OpenVPN and DS718+, it went like a dream and “What-is-my-IP” confirmed that I am in full-tunnel mode via the client’s fixed IP
My client already uses his Server from home to his office after hours with WebDAV but also now wants to use an office printer from remote(his home). Although I am in the remote network, I see nothing of the remote networks’s assets.
What am I missing??
LG aus München
If you can see all devices connected to that network, you should be able to print, though I admit that I’m not an expert on printers/printing through VPN. It could be a routing issue on the destination side (where VPN server is located), but that’s really just a guess if I’m being honest.
Hey Frank. Thank you for the step by step tutorial. Everything seems to be working as expected. I have one question though. After setting up DDNS and OpenVPN, is it correct, that I can access my NAS through these three methods?
1) hostname.synology.me:xxxxx
2) xx.xxx.xxx.xxx:xxxxx (External Address (DDNS) + Port)
3) xxx.xxx.xx.xx:xxxxx (NAS IP Address + Port)
If outside of my own network, I would connect to the VPN and use method 3) to access my NAS.
When entering 3) without anything prior to the IP Address, I get “400 Bad Request – The plain HTTP request was sent to HTTPS port” I have to enter “https://xxx.xxx.xx.xx:xxxxx” (NAS IP Adress + Port) to get access. This shows a warning as no certificate exists. Is this correct? In your video, which explains the setup, you’re not entering “https://”
I’m looking forward to your reply. Thanks!
With OpenVPN, you will access your NAS the way you normally access it on your home network. So technically, the first two options will not work unless you port forward the DSM port (which isn’t recommended). How do you access your NAS? If it’s by local IP address, that should function when you try and access it. As for the 400 error, just change the URL to HTTPS instead of HTTP (https://LOCAL_IP:%5BPORT%5D).
Hi WunderTech! First off I want to thank you for all your tutorials. They have been amazing in assisting me with properly securing my Synology DS220+ NAS. I am currently trying to set up OpenVPN and am having issues with certificates. I’ve followed the tutorial to the letter. I have checked to see that my port 1194 is open using the ipvoid port scanner and it is indeed open. I have added “client-cert-not-required” into my VPNConfig.ovpn file that was generated by exporting my configuration. It appears that it is connecting to my server, but it is failing the certificate verification. See error log below. I have replaced my IP with XX’s in the log. Any insight would be greatly appreciated, thanks!
⏎[Oct 10, 2021, 07:07:36] Frame=512/2048/512 mssfix-ctrl=1250
⏎[Oct 10, 2021, 07:07:36] UNUSED OPTIONS
1 [tls-client]
3 [pull]
5 [script-security] [2]
⏎[Oct 10, 2021, 07:07:36] EVENT: RESOLVE ⏎[Oct 10, 2021, 07:07:36] Contacting XX.XXX.XXX.XXX:1194 via UDP
⏎[Oct 10, 2021, 07:07:36] EVENT: WAIT ⏎[Oct 10, 2021, 07:07:36] WinCommandAgent: transmitting bypass route to XX.XXX.XXX.XXX
{
“host” : “XX.XXX.XXX.XXX”,
“ipv6” : false
}
⏎[Oct 10, 2021, 07:07:37] Connecting to [XX.XXX.XXX.XXX]:1194 (XX.XXX.XXX.XXX) via UDPv4
⏎[Oct 10, 2021, 07:07:37] EVENT: CONNECTING ⏎[Oct 10, 2021, 07:07:37] Tunnel Options:V4,dev-type tun,link-mtu 1602,tun-mtu 1500,proto UDPv4,comp-lzo,cipher AES-256-CBC,auth SHA512,keysize 256,key-method 2,tls-client
⏎[Oct 10, 2021, 07:07:37] Creds: Username/Password
⏎[Oct 10, 2021, 07:07:37] Peer Info:
IV_VER=3.git::c2153df1
IV_PLAT=win
IV_NCP=2
IV_TCPNL=1
IV_PROTO=30
IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
IV_LZO_STUB=1
IV_COMP_STUB=1
IV_COMP_STUBv2=1
IV_GUI_VER=OCWindows_3.3.2-2475
IV_SSO=openurl,crtext
⏎[Oct 10, 2021, 07:07:37] Transport Error: OpenSSLContext::SSL::read_cleartext: BIO_read failed, cap=2576 status=-1: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
⏎[Oct 10, 2021, 07:07:37] EVENT: CERT_VERIFY_FAIL OpenSSLContext::SSL::read_cleartext: BIO_read failed, cap=2576 status=-1: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed⏎[Oct 10, 2021, 07:07:37] EVENT: DISCONNECTED ⏎
I believe that your synopsis is correct. One thing to check is the certificate that OpenVPN is using on your NAS. If you go to Control Panel > Security > Certificates > Configure, are you using the default “Synology” certificate or are you using a different one? If it’s a different one, can you try replacing it with the Synology one and exporting a new config file, then retrying?
Hi Frank, I’m almost ready to test OpenVPN with my current laptop but I have a question that I didn’t find the answer :
How do I configure my Synology applications on my laptop so that they will continu to work on my laptop when I’m at home and when I’m on the go ?
I know that I can toggle the OpenVPN on and off, but maybe I did something wrong, I configured for example Synology Photo to use 192.168.2.140 for exemple on my LAN on my iPhone to upload my pictures when I start the app?
Do I need to use all the time the DDNS named like @synology.me so that the Synology apps are able to switch from a non VPN network to when I’m outside of my house ?
Thanks for your help !!!
Hello! No, in order for it to work, you would basically use the local IP address (the same local IP address you use when you’re home – 192.168.2.140) from wherever you are. Basically, when you connect to OpenVPN, the application will work the same way as when you’re at home (assuming it connects properly). DDNS will not be used anywhere other than the OpenVPN Configuration file.
I have configured OpenVPN but it only work in same network as NAS network. But from my mobile network it is not working.
I have two routers connected in series. Do I need to open port on both the router? Is multiple router can cause the issue?
Double NAT (which is what that is) can cause a lot of problems. You can try port forwarding on both, but the chances are you’ll still run into problems. Have you looked into Tailscale?
The purpose of dual router is to extand converage to next house. But I only use primary router(ISP). Can I disable NAT on secondary router and still everything works fine and I can also user OpenVPN?
I have already forwarded OpenVPN porn on both the routers. I will use Tailsale as last option but I preferred OpenVPN.
If you put the second router in bridge mode, it should do exactly what you’re looking for.