In this tutorial, we’re going to look at how to create an app password in Office 365.
Before we start, it’s important to understand exactly what an app password does. After implementing Office 365, there are specific services that require a password but won’t work with two-factor authentication. In cases like this, app passwords can be used which will bypass the configured two-factor authentication.
An app password is a longer password (for security purposes) that is randomly generated. Once again, this password can be used in circumstances where two-factor authentication won’t work.
How to Create an App Password in Office 365
Before you try to create an app password, please be aware that two-factor authentication must be enabled. If it’s not enabled, simply using the password will work.
1. Navigate to the Office 365 Portal.
2. In the top right, select your initials and then select View Account.
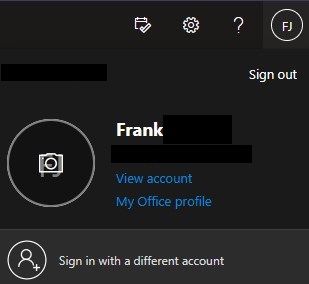
3. On the left-hand side, select Security Info.
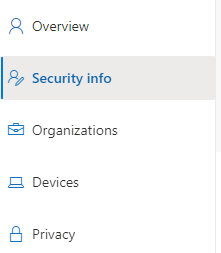
4. The default sign-in method will show here. Select Add Sign-in Method to create an app password. NOTE: This is also where you can set up two-factor authentication if you’d like (utilizing a phone number or authenticator application).
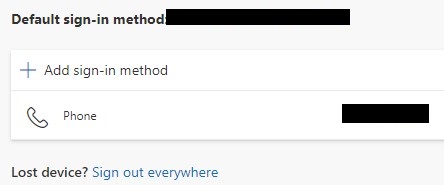
5. Select App password and then select Add.
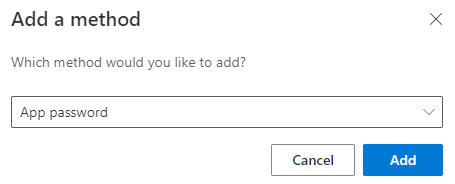
6. Enter a description so you’ll know exactly what this app password is used for.
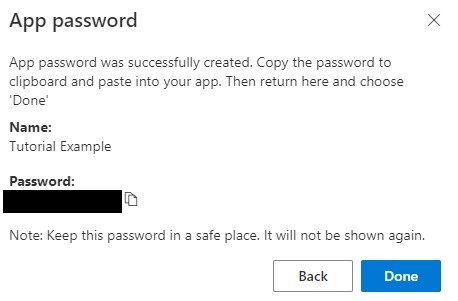
7. The next screen will now contain the app password. Copy the password to your clipboard and then select Done.
Please be aware that this is the first and last time you’ll be able to see this app password, so add it to a password manager or somewhere secure to be able to use it in the future.
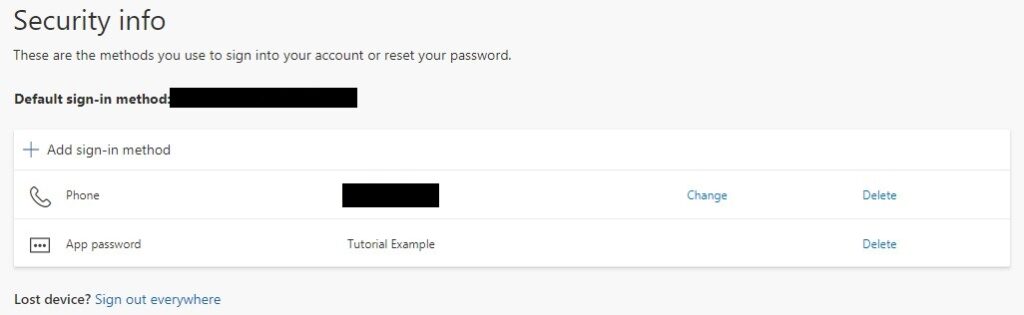
8. At the Security Info screen, you’ll now see the two-factor authentication that’s enabled, as well as the app password.
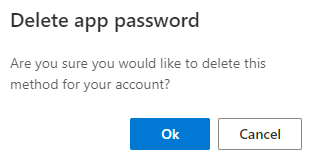
9. If you ever want to delete the app password, you can do so on the page above by selecting Delete, then confirming by selecting Ok.
Office 365 App Password Best Practices
It is in your best interest to utilize one app password per service that you’re using. This allows you to individually remove passwords if you stop using a specific service.
If you think about a scenario where you utilize only one app password, you’ll have to remember all of the locations where that password is used if it ever needs to be changed or removed. Separating them out individually will solve that potential problem.
Conclusion & Final Thoughts
The process above will work if you have multi-factor authentication enabled through Azure AD as well, but please be aware that app passwords must be enabled for your tenant.
The app passwords configured here do not expire, meaning that it’s in your best interest periodically check and confirm that the passwords configured are still needed and being used.
Thanks for checking out the tutorial. If you have any questions, please leave them in the comments!
