In this tutorial, we will look at how to connect a Raspberry Pi to a WireGuard VPN Server.
I use Raspberry Pi devices for various different things with some of them being used off-site. Something that runs constantly is the Raspberry Pi I use to backup my Synology NAS off-site. I’ve always used OpenVPN for this, but after setting up and configuring WireGuard, I was interested in using WireGuard as my VPN protocol for my off-site backup.
The thing with WireGuard is it’s almost nothing like OpenVPN. The concept of client devices and server devices isn’t valid which makes accomplishing this task somewhat different than most people are used to. The good news is that it’s very simple to set up and configure. The majority of it is done by running a few commands and adding your config file, but there’s very little information online that will show you exactly how to do this. After you configure the WireGuard server on a Raspberry Pi stored on your local network, the instructions below can be used to configure a Raspberry Pi to automatically connect to that VPN server every time it’s turned on!
Instructions – Connect Raspberry Pi to WireGuard VPN Server
1. Run the commands below, in this specific order. To sum up, we are adding the WireGuard Debian installation source and then ensuring that it’s not used for regular Raspberry Pi OS packages. We’re then installing WireGuard.
echo "deb http://deb.debian.org/debian/ unstable main" | sudo tee --append /etc/apt/sources.list
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 04EE7237B7D453EC
sudo apt-key adv --keyserver keyserver.ubuntu.com --recv-keys 648ACFD622F3D138
sudo sh -c 'printf "Package: *nPin: release a=unstablenPin-Priority: 90n" > /etc/apt/preferences.d/limit-unstable'
sudo apt-get update
sudo apt install wireguard
2. After we’re done installing WireGuard, we need to install the WireGuard tools. This, along with WireGuard, is how we will connect back to our WireGuard VPN Server.
sudo su
apt install raspberrypi-kernel-headers libelf-dev libmnl-dev build-essential git
git clone https://git.zx2c4.com/wireguard-tools
make -C wireguard-tools/src -j$(nproc)
make -C wireguard-tools/src install
3. Since we’re only connecting back to our VPN Server, we need to create a file where we will store our VPN profile information. To be clear, this is generated on the VPN server side. We are only copying the contents of the file so that we can authenticate with our VPN server. Create the file, add the contents, and then save the file.
nano /etc/wireguard/wg0.conf
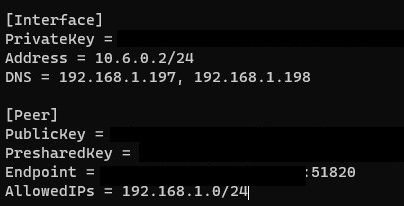
At this time, you have two different options. If you only want to connect to the VPN server, you can run the command below to connect. NOTE: The line below it in purple is what you will use to disconnect from the VPN.
wg-quick up wg0
wg-quick down wg0
If you want to connect to the VPN every time the Raspberry Pi is turned on rather than using the commands above, simply run this command and restart.
sudo systemctl enable wg-quick@wg0
There are a few additional items that you want to ensure that you have configured before restarting.
- Since this Raspberry Pi will most likely be remote, it’s a good idea to configure a persistent connection so that it doesn’t disconnect from the VPN.
- This configuration will allow you to connect FROM your external network TO your local network. Your local network will be unable to connect to your external network if you don’t configure a static route. This is a very important step that a lot of people miss!
Conclusion
This tutorial is very basic but it’s super powerful. There are so many different things you can do with Raspberry Pi devices. Having the ability to automatically connect to your home network safely and securely will give you so many options.
Thanks for reading. If you have any questions, please leave them in the comments!



Hi. Looks simple enough, thanks!
One question though: if I want to use Pi in my local network as a gateway to connect to a vpn service like mullvad, is it the same procedure?
I also want to be able to connect a few devices through this vpn gateway so those devices use the mullvad vpn tunnel…
Thanks for reading!
I unfortunately don’t have much experience with Mullvad so it’s hard for me to comment. The WireGuard VPN server is really setup so that you can connect to your local network from an external network, where it appears like Mullvad is used for privacy purposes. If Mullvad offers a WireGuard service (some providers do), you will have to follow their instructions to set it up.
Not sure how much this helps, but let me know if I can answer any other questions!
Yeah, mullvad has config files for Linux. Their guide is very simple though. It doesn’t deal with the fact I need to open up the wireguard client on the pi so other devices on the lan can use that tunnel. Also, my pi is located in a place where i can not hook it up with monitor, keyboard and mouse. I have to use SSH from a pc on my lan. I’ve managed to get the wireguard vpn to work. However, when the wireguard tunnel is active the ssh connection breaks.
Maybe a project for you? 🙂 I’m surprised i haven’t found any real guides out there for people wanting to use a Pi as a wireguard gateway to connect local network devices to a vpn provider? Would surely be useful for a lot of people…
I will add it to my list and hopefully get to it! I haven’t used mullvad but I will look into it!
I have this problem:
Your kernel headers for kernel 5.4.72-v8+ cannot be found at /lib/modules/5.4.72-v8+/build or /lib/modules/5.4.72-v8+/source.
What model Raspberry Pi are you using? You might have to update the kernel headers and try again. Let me know if this doesn’t work and we can continue troubleshooting!
https://www.raspberrypi.org/documentation/linux/kernel/headers.md
I have same problem with RPI 2
This might sound like a backwards solution, but try and run the PiVPN installer to install WireGuard. You can find instructions here: https://www.wundertech.net/setup-wireguard-on-a-raspberry-pi-vpn-setup-tutorial/
During the installation, there’s a step that will update your kernel if necessary. After the kernel installation finishes, you’ll need to reboot your NAS. Reboot your NAS and then try this tutorial again.
Let me know how it goes and we can continue to troubleshoot!
Great article! One question: Is it possible to have a raspberry pi become a vpn router and also have the wireguard client software installed? This way all the traffic of hosts connected to the “client pi” would go through the remote vpn server pi.
Thank you! I don’t think that you can have the VPN server be both, a VPN server and the client to another server. My reasoning is that they both use the wg0 network interface to do their routing, so you’d be trying to listen on the same NIC that you’re trying to connect to a separate server. This tutorial is actually a different way of setting up the client as opposed to using PiVPN. If you use PiVPN and change the wg0.conf file, you will be able to connect as a client as well.
I could be wrong, but this is my initial thought. If I can answer any other questions, please let me know!
Thank you for the quick response! It’s nice to see a different way of setting it up other than PiVPN. Just to clarify my setup, I have two Raspberry Pi 4’s at different physical locations. I installed WireGuard on both and set one as the server and one as the client. Can I turn the client running the Wireguard client into a VPN router? This way all the traffic of hosts connected to the client Pi is directed to the server Pi. Sorry this is a little out of scope of the article – all the resources online seem to use an OpenVPN server and client for this setup.
Not a problem! I am a little confused on what you mean by the “devices connecting to the client Pi are directed to the server Pi”. Since the end goal is to get to the server, wouldn’t you have all the devices that you’re trying to connect to the client Pi automatically connect to the server instead?
If you mean that the devices on the same LAN as the client Pi automatically be routed to the server Pi, I don’t think this is an option. They would need to connect to the server Pi in some capacity.
Hope this makes sense, but let me know if you have any other questions!
Hey WunderTech, I meant more like the client Pi would be a wifi access point (like a router) that multiple devices would connect to in order to access the server. I think this resource describes what I mean: https://blog.stigok.com/2019/03/26/raspberry-pi-wifi-ap-wireguard-port-53.html
Were you referring to this situation when you said “devices on the same LAN as the client Pi automatically be routed to the server Pi”? If so, why would this option not be possible? Thanks for your help!
Sorry, I didn’t mean to imply that it was or wasn’t possible. I just unfortunately don’t have experience doing it, so it’s hard for me to comment on how it should be done.
I am making a total assumption that you could probably alter the approach in that article you linked to do what you’re looking, but it’s hard for me to validate it. I know this doesn’t help much, but if I can answer any specific questions, please let me know!
Hi Wundertech,
Great video’s on youtube.. keep on going.
Question: Can i use the Wire-VPN (installed on the raspberry pi3) to run program’s ON the raspberry to go through the VPN?
Thanks in advance for your answer.
Thanks for the kind words!
If you mean connecting the Raspberry Pi to a WireGuard VPN server (as a client) and having applications on it be accessible to machines where the VPN server is set up, yes. You will need to configure a static route though so that your local network (where your VPN server is located) will know how to reach the VPN devices. Those instructions are here: https://www.wundertech.net/setup-wireguard-on-a-raspberry-pi-vpn-setup-tutorial/#static-route
If I’m misunderstanding your question, please let me know and I will get back to you!
I’ve been researching for a few days now. Can’t seem to find a solid tutorial. Yours seems to be leaning in the right direction. I think Craft Computing came really close too [https://youtu.be/xFficDCEv3c]. Essentially, I’m looking to do (3) things with a RPi4.
1. Act as WireGuard VPN Client that connects to a commercial VPN service (PIA, TunnelBear, TorGuard, etc.)
2. Become a secondary VPN router on my main network. Connect multiple devices to said pi though either wifi, or ethernet (wired connection + usb connection).
3. Also filter ads through PiHole
Please note that I’m extremely green to this scene and just know enough to know that these technologies are out there in one form, or another. If this was an x86 device, pfsense should be able to do all of these things. Conceptually, there are a few opportunities for ambiguity; for instance, PiHole acts as a server itself not sure if you can act as a router and a separate server on the same device.. Maybe you could? If all the packages were setup in docker containers? That way, you could virtualize a mini network inside of the Pi. I think..? Otherwise, I may need to get another Pi just to utilize PiHole for the devices that I want to add VPN services to. I don’t see why you can’t use (1) Pi for all of this, but there is literally not complete tutorials on this sort of thing. Any help and input is certainly appreciated!
Setting up scenarios 2 and 3 are actually fairly straight forward. If you implement Pi-Hole before installing WireGuard, it will ask you if you’d like to use Pi-Hole as the DNS server. At that point, the clients that you create will automatically connect to Pi-Hole and your local network will be able to use the Raspberry Pi’s IP address to use Pi-Hole as their DNS server. I have this set up and it’s fairly straight forward.
Where I think you might have problems is implementing 1 and 2 on the same device. Since WireGuard functions more like a router and creates its own network interface (wg0) to do the routing, a standard Raspberry Pi most likely wouldn’t work, but this is an assumption on my part. If you had a device with two NIC’s, I’d imagine you could use one for scenario 1 (wg0 to eth0) and one for scenario 2 (wg0 to eth1) and it would work as you’re expecting. It’s hard for me to say as I’m not subscribed to any public VPN providers, but that’s at least how I’d imagine it.
I’m not sure if this helps or makes things worse, but if I can answer any other questions, please let me know!
I tried to make a working backup of the SD card I configured (and was working). But the backup card would not work. So I configured a separate PiVPN user on the server and cut-and-pasted it into:
nano /etc/wireguard/wg0.conf
The new card would connect to the host PiVPN just fine, but with a different IP address (10.6.0.4 for initial card, 10.6.0.11 for the backup card).
Make sense?
The IP address that you connect with is in the configuration file of WireGuard. OpenVPN uses a dynamic IP address but WireGuard forces you to manually define it. Is that what it’s showing in the config file?
Let me know!
Hi WunderTech,
Great tutorial. I’m using Wireguard to provide a secure connection from an offsite RPi4 being used as a Hyper Backup target for my Synology NAS. I believe a mash up of this video and another one you did (could not get OpenVPN to work for the life of me). I’m about 98% there. Using a hotspot, my RPi is able to connect to my Wireguard server on my LAN and I can ping and see everything of the network from the Pi. However, I can’t get to the Pi from my network, and the Synology can’t see the Pi as a Hyper Backup target.
I setup a static route, but I must have it misconfigured. My Wireguard server is 192.168.1.205 and my offsite RPi has an IP of 10.6.0.3. I have a Ubiquiti Unifi router, and have the static route destination network set as 10.6.0.0/24 and the next hop as 192.168.1.205. No joy. Can’t ping 10.6.0.3. My router is 192.168.1.1. Not sure if I should be using anything other than the offsite RPi IP address and the Wireguard server IP (also a RPi4 if it matters).
Appreciate the time.
You are correct in stating that it’s most likely the static route. If I understand this properly, the WireGuard VPN Server is running on your local network (where the NAS is) and the off-site Raspberry Pi is connecting back to the WireGuard VPN Server?
One weird question – after you setup the static route, did you reboot your WireGuard server? If you didn’t, can you try that? I had major problems when initially setting up my static route and rebooting the server fixed them (I tried everything, but that). My assumption is that it needs to get the new configuration and the reboot forces it to.
Let me know and we can continue troubleshooting.
Yea, dead on summary. I rebooted the Wireguard server, but still can’t ping my local network from the hotspotted RPi. The one place I didn’t follow your tutorial to the letter was the iptables. I’ve been using a full tunnel VPN and didn’t seem to need them (I’ve had the WG server up and running for a few weeks now. Your video on setting up the server was great). I went back and added them to the wg0.conf file and that seemed to do the trick. Of course, I rebooted then too, so who knows 🙂
Anyways, thanks for the prompt response. I enjoy the YT channel and the content you produce!
That’s awesome! I’m glad to hear that you were able to get it resolved. Thanks for the support!
Hey Wundertech,
thanks so much for your blog piece – this is exactly what I was looking for!
May I ask a few questions?
Here’s my planned scenario:
– WireGuard Server on my local Synology (VMM, 24/7) to be backed-up to a remote Syno
– remote Syno will receive WireGuard-tunneled backup (once a week)
– remote Router will have the Raspberry attached acting as the WG-Client
– the remote Raspberry is already running Pi-Hole + Unbound to filter all networking traffic
– as I understood, I would then only need to forward the WG-Port on the (remote) target router to the attached Raspberry (to enable the WG-Client on the Raspi work „for“ the Synology) and give WG the Raspi’s IP für DNS (PiHole) plus have a DynDNS address active in the router
My questions:
a) Would I need to setup something in addition to the above (aside from giving the Raspi the WG-Config produced on the WG-Server (local Syno))?
b) When I install the WG-setup on the remote Client-Raspberry, would I destroy the existing OS (running Pi-Hole + Unbound) or would installing the Debian installation source in your first step work „beside“ the Pi-Hole + Unbound?
c) Would you recommend to use a persistent connection (PersistentKeepalive=25) in the config for the remote Raspi WG-Client, even if the remote Syno will be bootet just once for the weekly backup routine?
Thanks so much again – can’t wait for the WG speed improvements :))
BR, Peter
Hi Peter!
I am doing my best to follow along, but I will be honest in saying that I’m clear on what you’re trying to accomplish, but not positive that your approach will or will not work, as I haven’t done this myself. I will do my best to answer your questions, but I want to highlight that so you take what I’m suggesting with a grain of salt!
A. If I understand it properly, you have WireGuard running on your Synology NAS in VMM. You want to back up this Synology to a remote Synology NAS. You’d first have to confirm that you’re able to access the remote Synology NAS. WireGuard works differently than OpenVPN, so there IS a chance that you will be able to access the Synology NAS through the connected Raspberry Pi, but since I don’t have this set up, it’s hard to confirm.
B. You shouldn’t destroy the existing OS, but if devices on that LAN are using it as their DNS server, you might run into problems when you connect it to your WG Server.
C. Yes, I would recommend using a persistent connection.
Depending on the technology that you’re using, it’s hard to say that one way will be better than the other. Another option that you have is IF you have a static external IP address, you can open the Hyper Backup port (or whatever application you’re using) and on the remote firewall, only allow access to that one external IP address. That will alleviate you having to mess around with WireGuard for the backups.
I know this isn’t the best answer and I apologize, it’s just hard for me say that it will or will not work as I don’t have this setup implemented. Let me know if I can answer any other questions!
Thanks Wundertech for your kind reply!
A. You already helped me a lot with your hint that WireGuard works differently than OpenVPN, will have to do “Trial and Error” anyway as soon I have setup the WG-Server on my local Synology.
No static adresses here, I have setup the Pi-Hole to have the router provide the DNS Server – the backup routine already works with a DynDNS address via both router’s IpSec protocol. Too slow TBH, that’s why I want to move to WireGuard.
I definitely come back to provide some feedback for readers planning similar/same setups.
Thanks much again, keep up your excellent blogging work with your special topics standing out from the crowd.
Not a problem! Excited to see how this turns out!
Hello Wundertech,
Thanks for this tutorial. This is the one I was looking for!
I stilk have some questions:
As James, I want to use this system to backup my QNAP Nas to another QNAP Nas outside my office.
As I do not want to open ports on my remote Nas, I want to set up a wireguard vpn connection from my remote location back to my office wireguard server.
Question 1: do I need to change the DNS on my remote router and set the remote IP local address from my remote RPI as DNS on the remote router? This way, all traffic will be routed thought the RPI (same principle as pihole).
Question 2: how will I find from my office the remote Qnap Nas?
Question 3: if from my remote location I force all traffic to go through the RPI (that will be connected as a client to the server), will I be able to see my office network? I have an old mac that no longer supports wireguard. I tried to install wireguard tools but it does not work and would like to access some folders on my office Nas.
Thanks a lot for your help.
Best
It sounds like you’re trying to implement a site-to-site VPN and have resources accessible on both networks, am I right in saying that? If so, you will have to set this up slightly different than the norm. I don’t have a guide on this (though it sounds like it would be great for a future video), but googling “site to site VPN wireguard” or something along those lines should tell you exactly what you’re looking to do.
I do apologize for not having better information, but I haven’t done this exact scenario so it’s hard to give input. With that said, let me know if I can answer any questions!
Hi, when I get to the nano /etc step I cannot save the wg0 file. Could you let me know what I’m doing wrong here? I liked your pivpn tutorial and now instead of using local apps on firesticks etc I want to use my second pi as a VPN gateway for my tv.
Thanks so much for any help here!
Can you try running it with sudo in front of it? sudo nano …
Hi, thanks very much! This got it working, and then playing around with routing tables I have 2 RPs in different countries, and managing to get my TV go through the RP to switch countries. This and your pivpn tutorials are really awsome, so thankyou! Just for indication, what kind of speed is to be expected with a wireguard RP server, ie if I have 10mb upload on the server is say 50% realistic? Anyway, thanks again! I am new to this stuff, but your tutorials really helped.
Glad that they help, thanks so much! The speeds will be extremely dependent on the upload speeds of the the networks where the WireGuard servers are set up – so in your case, yes, I’d say that anywhere from 50-60% is normal.